hiden wav
rot47+rot13解密后得到隐藏flag在wav文件中的脚本
import wave
with open('flag.txt', 'rb') as f:
txt_data = f.read()
file_len = len(txt_data)
txt_data = file_len.to_bytes(3, byteorder = 'little') + txt_data
with wave.open("test.wav", "rb") as f:
attrib = f.getparams()
wav_data = bytearray( f.readframes(-1) )
for index in range(len(txt_data)):
wav_data[index * 4] = txt_data[index]
with wave.open("hiden.wav", "wb") as f:
f.setparams(attrib)
f.writeframes(wav_data)
根据加密的脚本询问下gpt跑出解密的脚本
得到flag
import wave
# Open the WAV file in read mode
with wave.open("hiden.wav", "rb") as f:
attrib = f.getparams()
wav_data = bytearray(f.readframes(-1))
# Extract the hidden data from the WAV file
hidden_data = bytes([wav_data[i] for i in range(0, len(wav_data), 4)])
# The first three bytes represent the length of the original text data
original_length = int.from_bytes(hidden_data[:3], byteorder='little')
txt_data = hidden_data[3:3+original_length]
# Write the extracted data to a new text file
with open('extracted_flag.txt', 'wb') as f:
f.write(txt_data)
print("The flag has been extracted and saved to 'extracted_flag.txt'.")
ok,now you find me,so the flag give you
DASCTF{12jkl-456m78-90n1234}
不一样的数据库_2
先是一个6位数字爆破,爆破出来密码是753951
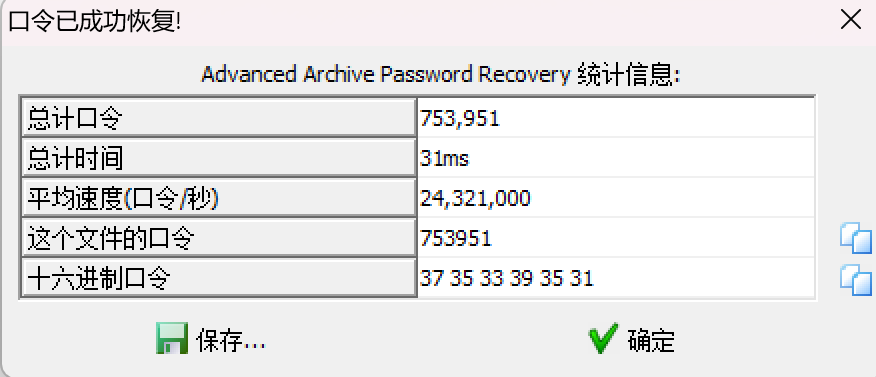
打开以后是个二维码缺了定位符,补全一下扫一下得到一串密码
NRF@WQUKTQ12345&WWWF@WWWFX#WWQXNWXNU
随波一把梭,看到了AES,推测经过凯撒变形了,AES开头的才是密码明文
即AES@JDHXGD12345&JJJS@JJJSK#JJDKAJKAH
压缩包里还有个文件Kee.kdbx,是windows的密码管理数据库文件,我们用Kee Pass打开后输入刚刚得到的密码即可进入数据库
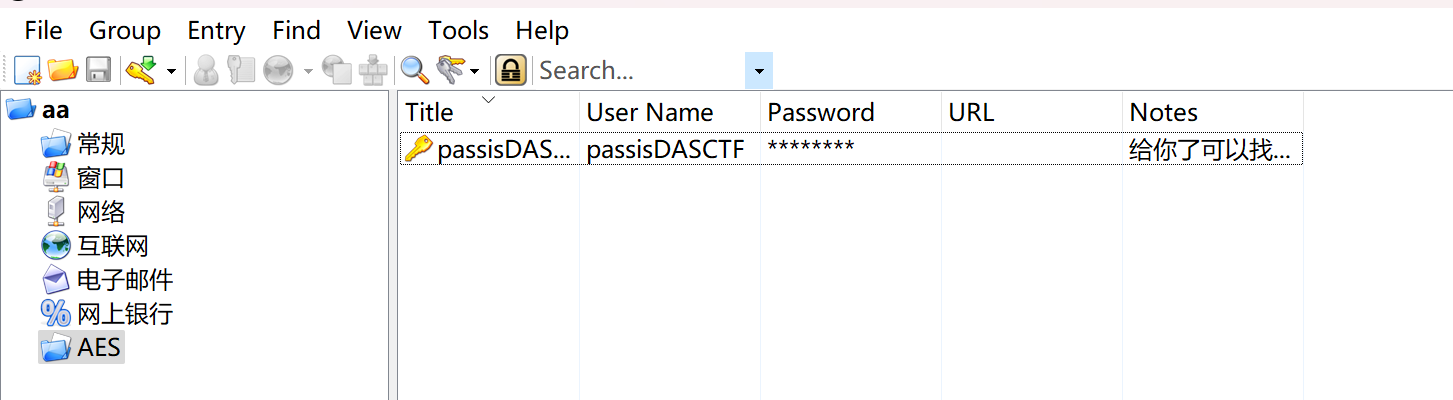
再Edit Entry
在历史选项中找到了历史文件有个AES加密的密文
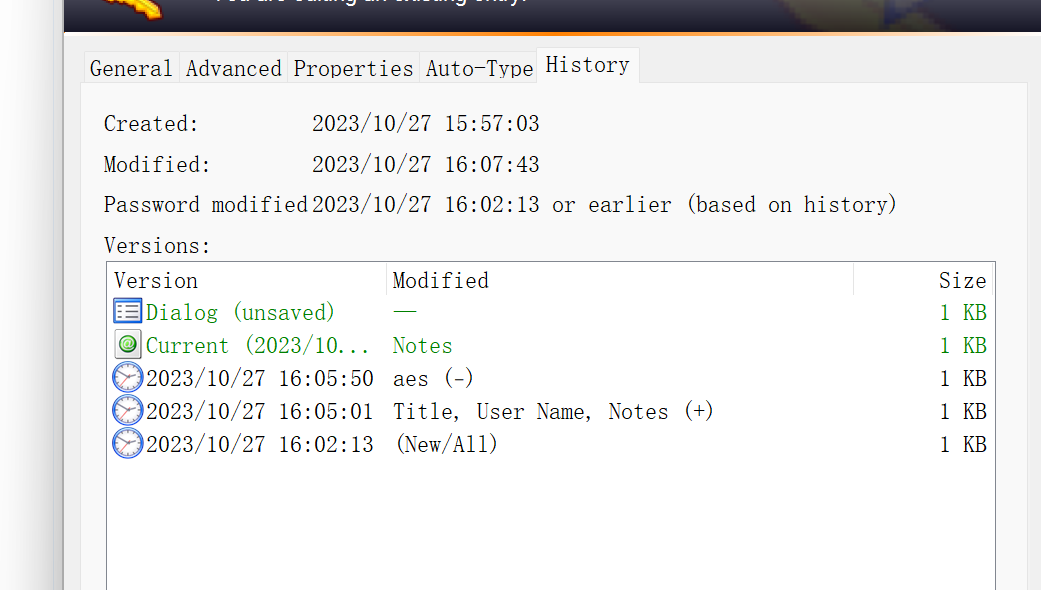
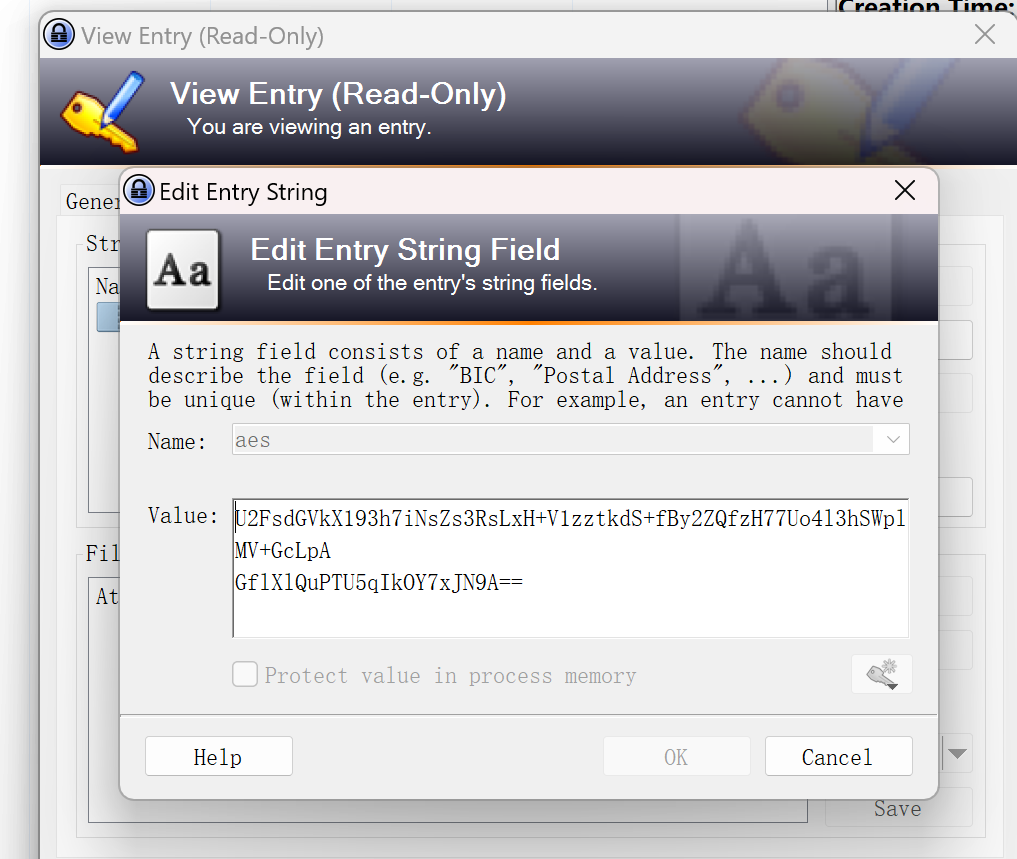
进去还能看到提示说pass是DASCTF,推测AES加密的密钥就是DASCTF,解密一下得到flag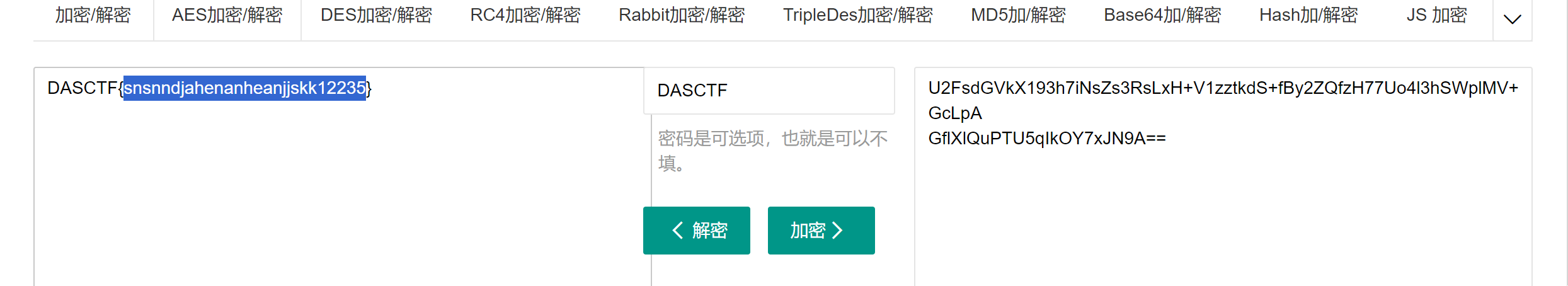
复现
Lyrics For You
环境还没开出来,nnd,啥时候能让我复现!!!